Self-service password reset (SSPR) is a feature introduced in Citrix ADC firmware 12.1.50.28. This feature grants users the ability to reset their own Active Directory passwords securely, from remote locations.
There is also an alternative self-service password reset feature that caters for internal users, not to be confused by ADC self-service password reset. The on-premises solution integrates with StoreFront and was first released in XenApp & XenDesktop 7.8. The configuration article for that feature is documented here.
Since the initial release of the on-premises self-service password reset, customers have asked for the same password reset capabilities to be available remotely, wherever the user was in the world. This has now been made via the 12.1.50.28 version of Citrix ADC. The feature is built on-top of the nFactor authentication engine.
Contents:
-
- 1. Requirements
- 2. Configure SSPR
- 3. Register as a user for SSPR (URL method)
- 4. Configure SSPR enforcement for unregistered users (attribute method)
- 5. Configure SSPR password reset
- 6. Reset password as a user
- 7. CLI commands – Force registration via attribute and password reset configuration with email verification
- 8. CLI commands – Force registration via attribute and password reset configuration without email verification
1. Requirements:
- Active Directory domain functional level of 2008, 2012 or 2016 required.
- nFactor authentication flow is the only way to configure SSPR.
- Registration is supported only through a web browser.
- An ADC Advanced (formerly NetScaler Enterprise) license is required at a minimum.
- AAA (Authentication, authorisation, and accounting) vServer required.
- An Active Directory attribute is required to store the encrypted registration information.
- The LDAP bind account must have write permission to the chosen attribute.
- The chosen attribute must support at least 128 characters and have a maximum value length of 32k.
Note: In this article, I have chosen userParameters as the attribute that will store knowledge-based authentication (KBA) and alternative email values. This article also assumes you are using a Gateway virtual server as part of your remote access offering to corporate users.
2. Configure SSPR
Scenario: Corporate users who wish to register for SSPR can do so by browsing to provisioned URL: https://unifiedgateway.jgspiers.com/register. This URL is accessible from anywhere in the world, and in a production environment will be configured with multiple factors of authentication.
Connect to the CLI of ADC and run command bind vpn global -userDataEncryptionKey unifiedgateway.jgspiers.com. Replace the unifiedgateway.jgspiers.com value with the name of your own certificate that is installed on ADC. Note, the key size of the certificate must be 1024 bits. There is a current bug in the 12.1.50.28 firmware that does not allow a larger key size to be used with SSPR. This is resolved in 12.1.51.16.
Edit your Gateway virtual server.
Make sure that no Basic Authentication policies are bound. We are using nFactor, so must use an AAA virtual server for authentication.
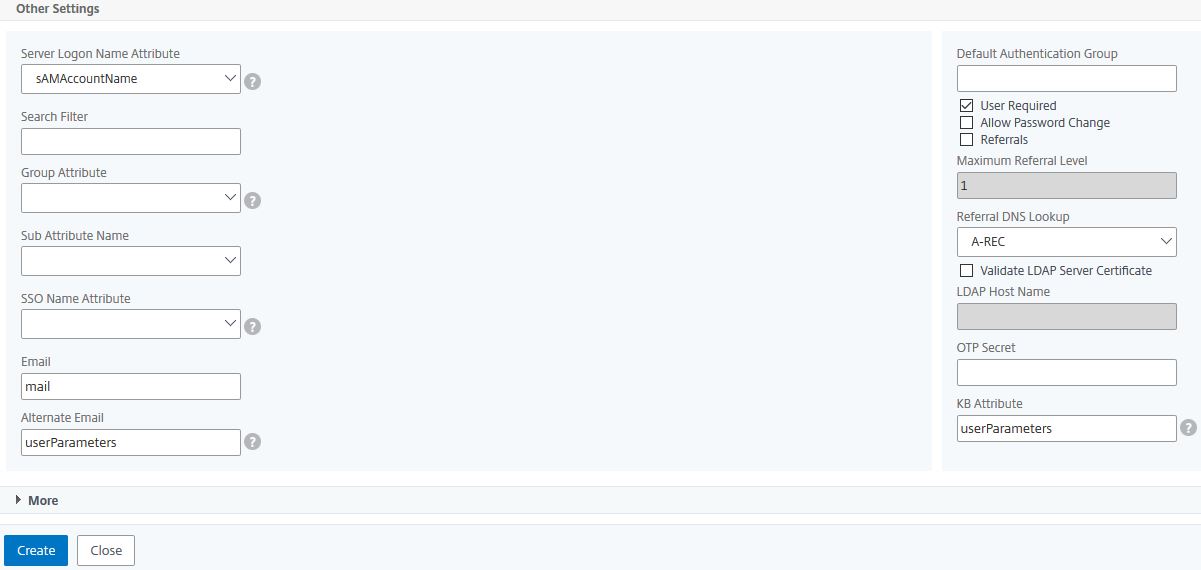
Navigate to Citrix Gateway -> Policies -> Authentication -> LDAP -> Servers -> Add.
Create an LDAP server as you normally would, similar to below. Name it SSPR-LDAP-Pol.
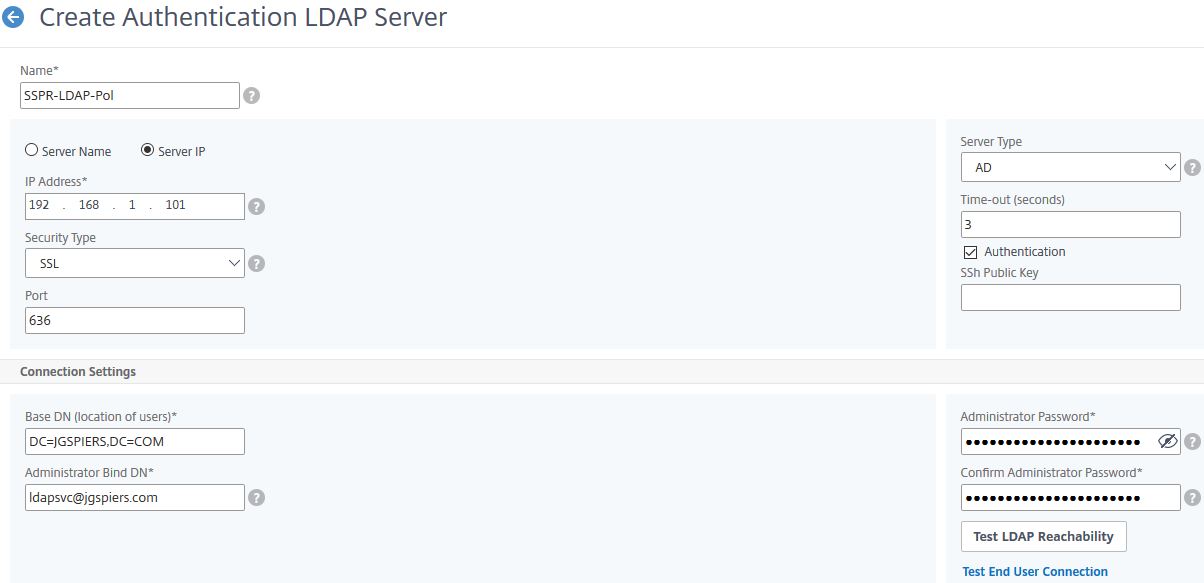
You will notice that two new fields have been added. Under KB Attribute and Alternate Email enter userParameters. If you have chosen another not-in-use attribute, enter that instead. Click Create.
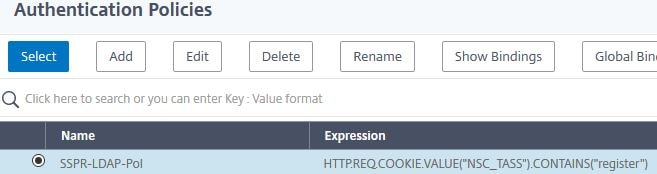
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Policy -> Add.
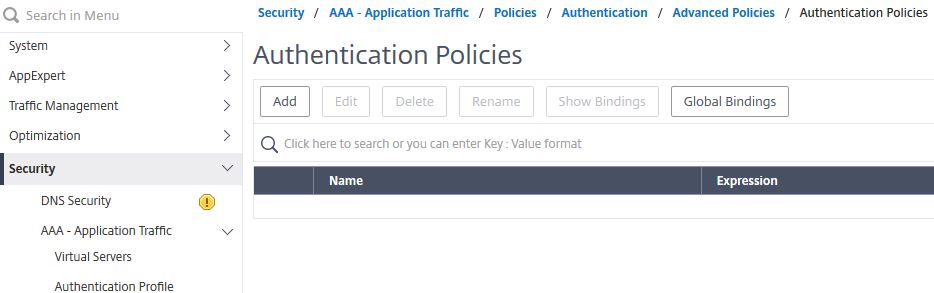
Enter the below information:
Name = SSPR-LDAP-Pol
Action Type = LDAP
Action = SSPR-LDAP-Pol
Expression = HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).CONTAINS(“register”)
Click Create.
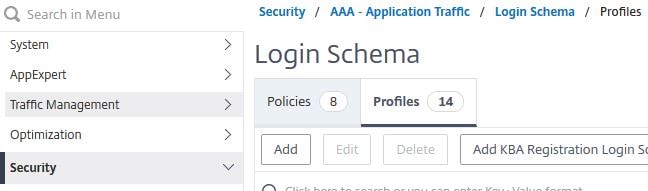
Navigate to Security -> AAA – Application Traffic -> Login Schema -> Profiles -> Add KBA Registration Login Schema.
Enter name SSPR-Registration-Schema. You now have the option of choosing up to four System Defined Questions. You can pick and choose what questions you want to make available to users, and they will be presented in a drop-down fashion during registration. If you configure two questions for example, then users are only required to pick two questions of their choice and provide answers to them.
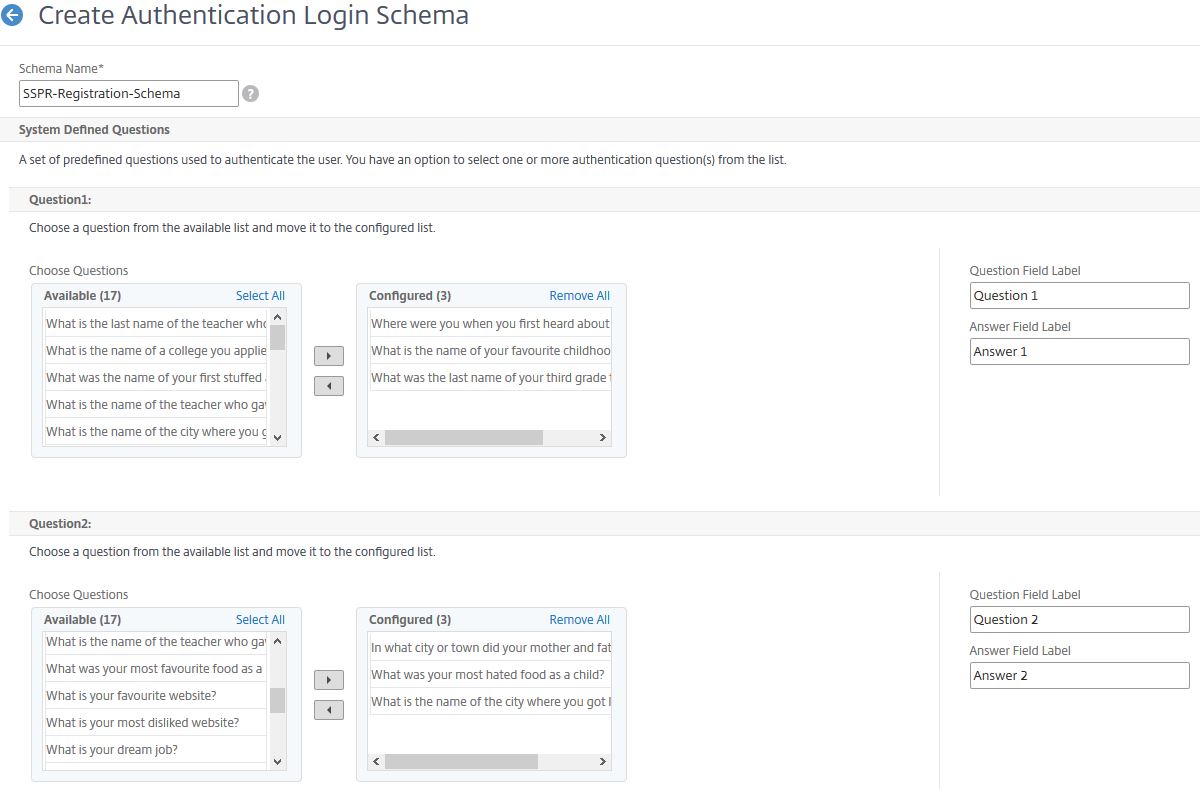
You can also choose to allow a maximum of two User Defined Questions. This allows users to pick their own questions and provide answers to them, in conjunction with the System Defined Questions.
Optionally, you can also select the Register Alternate Email checkbox. If selected, users during KBA registration will be prompted for an email address, which is stored in the attribute you specified during LDAP server creation. This feature is for added security. Users who are resetting their password will not only have to answer the security questions but complete an OTP (one-time password) validation before their password reset is successful.
Click Create.
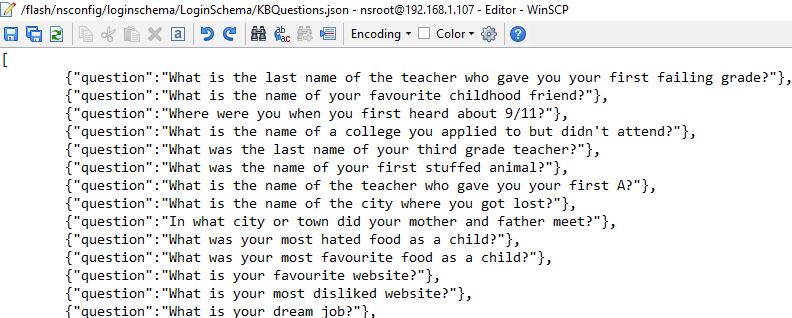
System defined questions are found under /nsconfig/loginschema/LoginSchema/KBQuestions.json. If you want to modify or add your own questions to this list, you can do so here.
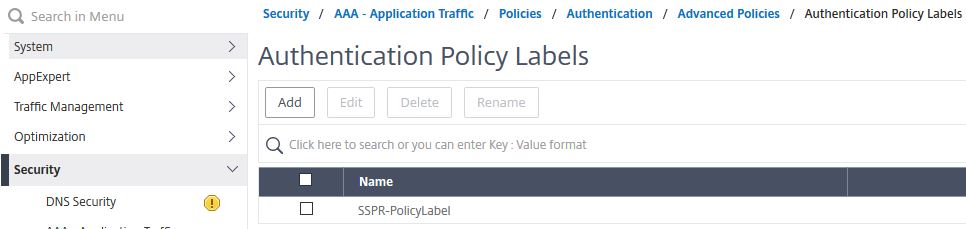
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> PolicyLabel -> Add.
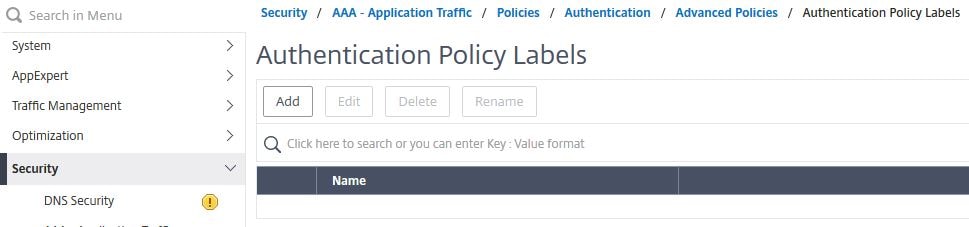
Enter the below information:
Name = SSPR-PolicyLabel
Login Schema = SSPR-Registration-Schema
Click Continue.
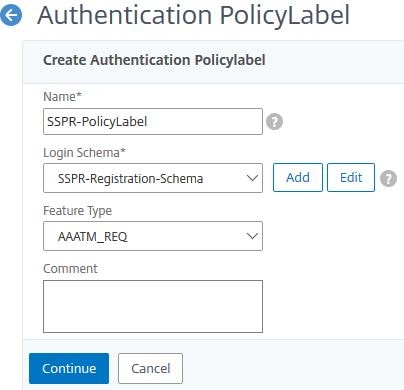
Click Click to select.
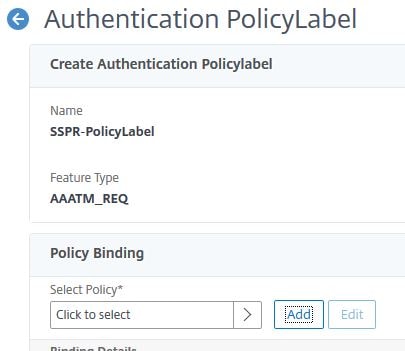
Select LDAP policy SSPR-LDAP-Pol. Click Select.
Set Goto Expression to END. Click Bind.
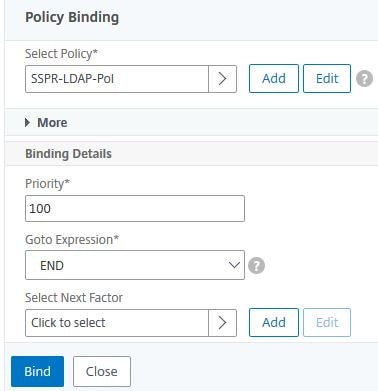
Click Done.
Navigate to Security -> AAA – Application Traffic -> Virtual Servers -> Add.
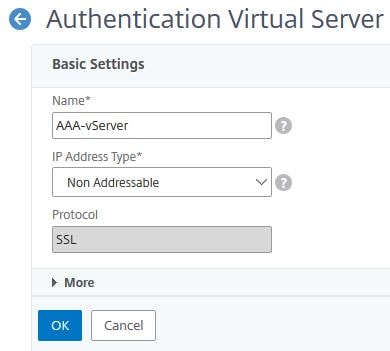
Enter the below information:
Name = AAA-vServer
IP Address Type = Non Addressable
Click OK.
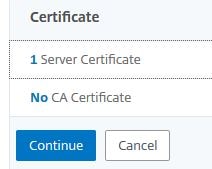
Click No Server Certificate.
Click Click to select.
Select the same certificate that is used on your Gateway virtual server. Click Select.
Click Bind.
Click Continue.
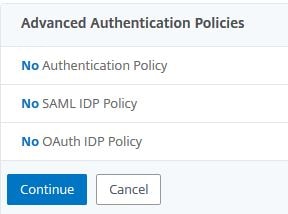
Click No Authentication Policy.
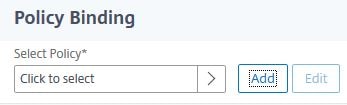
Click Click to select.
Select LDAP policy SSPR-LDAP-Pol. Click Select.
Click Click to select under Select Next Factor.
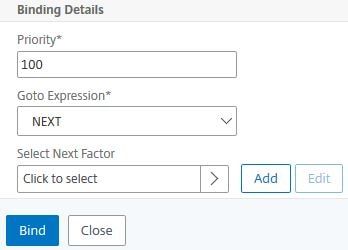
Select Policy Label SSPR-PolicyLabel. Click Select.
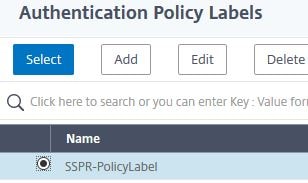
Click Bind.
Click Continue.
Click Done.
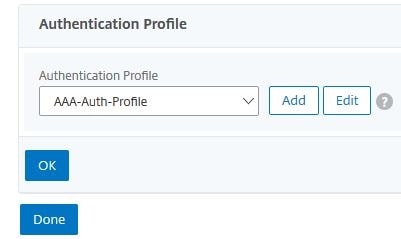
Navigate to Security -> AAA – Application Traffic -> Authentication Profile -> Add.
Enter the below information:
Name = AAA-Auth-Profile
Choose Virtual Server Type = Authentication Virtual Server
Click Click to select.
Select virtual server AAA-vServer. Click Select.
Click Create.
![]()
Navigate to Citrix Gateway -> Virtual Servers and edit your Gateway virtual server.
Under Authentication Profile, using the drop-down, select AAA-Auth-Profile. Click OK followed by Done.
3. Register as a user for SSPR (URL method)
Now that the configuration is complete, you can have users register with SSPR.
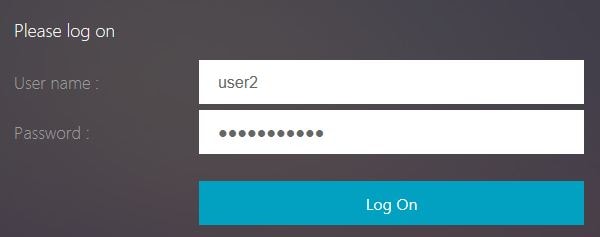
Open a web browser and navigate to your Gateway URL, with /register appended to the URL.
Enter your username and password. Click Log On. In a production environment, you will have multiple factors of authentication.
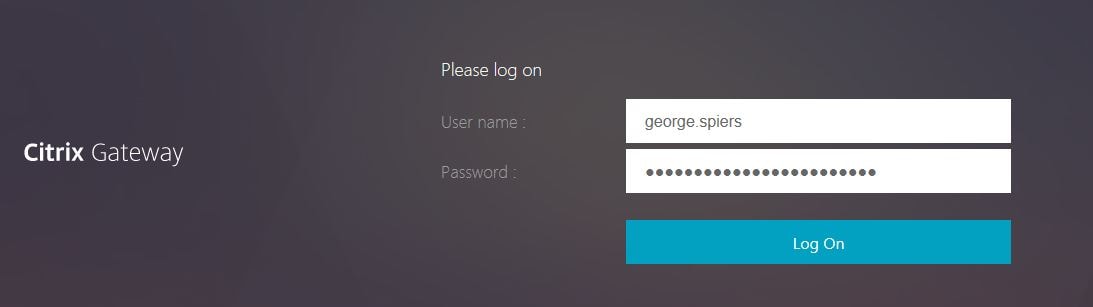
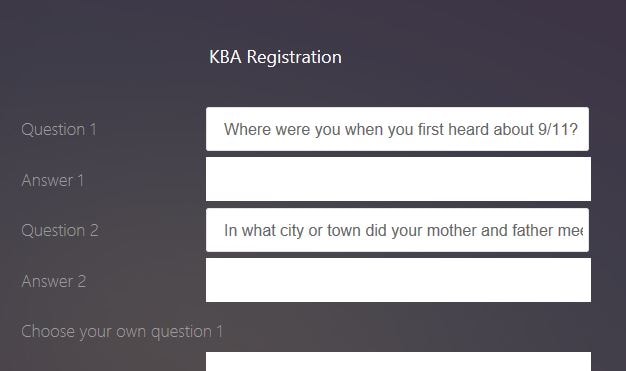
The KBA Registration page is displayed. The page is made up of System/User Defined questions and an alternate email ID.
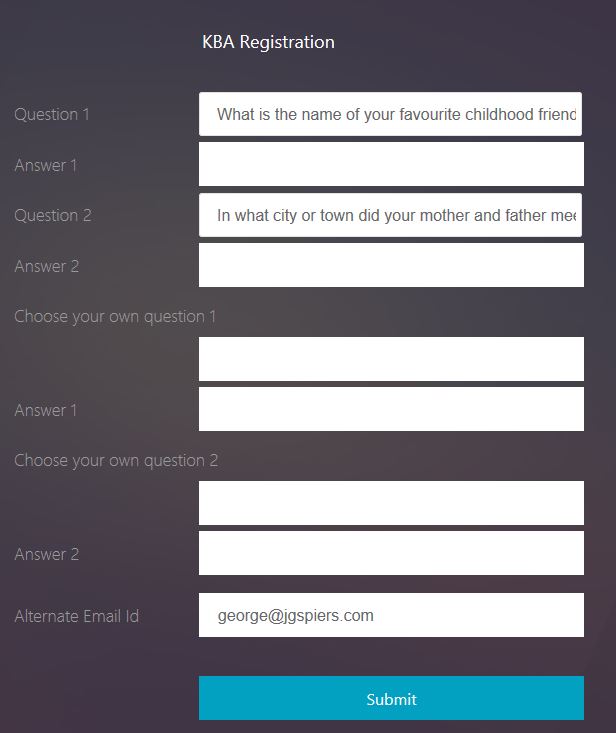
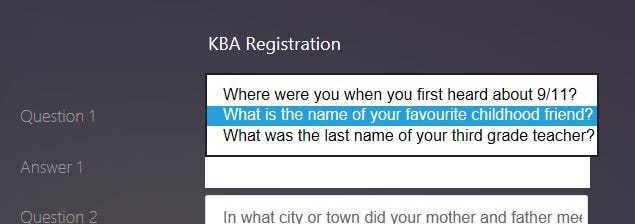
You can use the drop-down boxes to select which questions you want to provide answers to as part of your KBA Registration. The questions available are the ones you configured in the earlier step when creating a KBA Registration Login Schema.
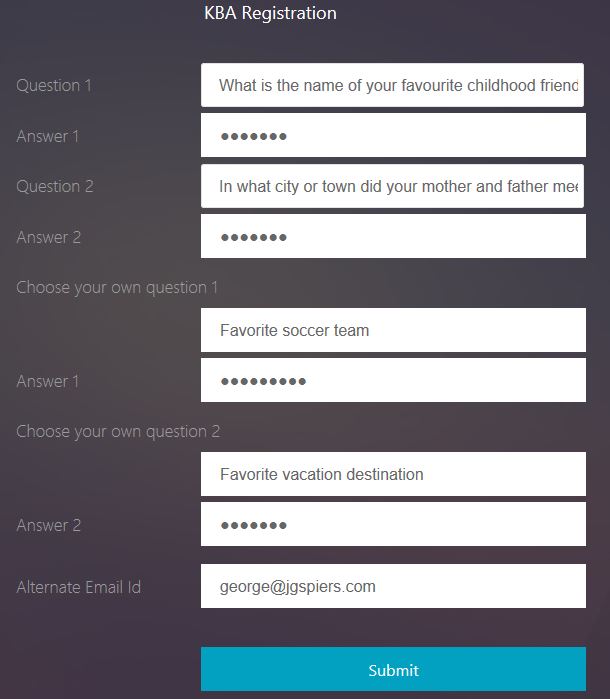
When finished selecting and answering questions, and providing an alternate email ID, click Submit. You will be passed through to Gateway.
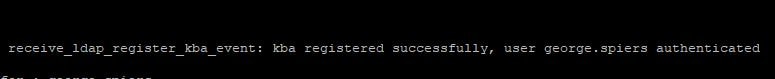
When reviewing AAA authentication logs, a kba registered successfully message is generated.
The userParameters attribute in Active Directory is populated with an encrypted value.
4. Configure SSPR enforcement for unregistered users (attribute method)
In the case you want to force users to register for SSPR, you can do so by having ADC evaluate if a user has previously registered. If no registration has been recorded, force the user to register before allowing them access to Gateway.
Scenario: Corporate users access Gateway remotely. If they are not found to have registered with SSPR, they are forced to do so before being allowed to access Gateway resources.
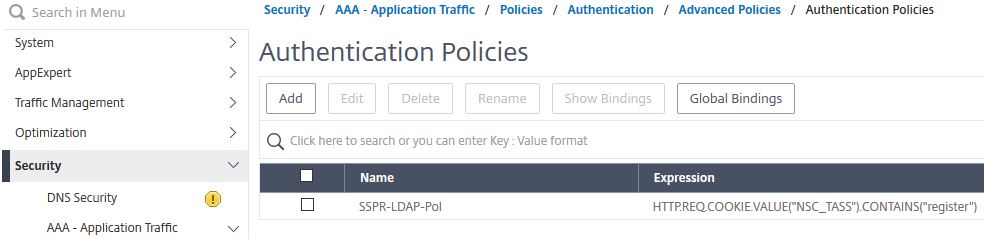
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Policy -> Add.
Enter the below information:
Name = LDAP_AllUsers
Action Type = LDAP
Action = SSPR-LDAP-Pol (created from previous step)
Expression = true
Click Create.
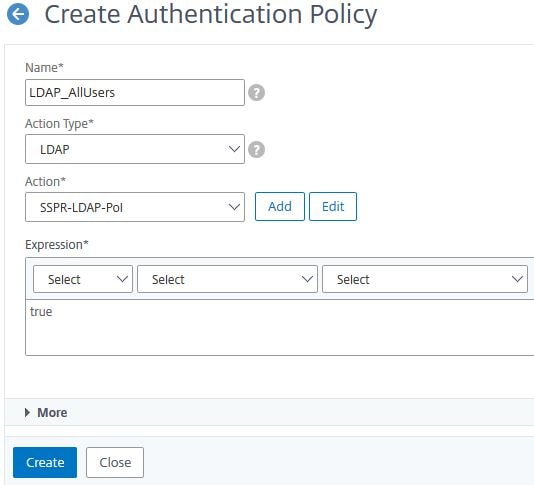
Create a second authentication policy. Enter the below information:
Name = SSPR-ForceRegister-NOAUTH
Action Type = NO_AUTHN
Expression = AAA.USER.ATTRIBUTE(“kba_registered”).NE(“1”)
Click Create.
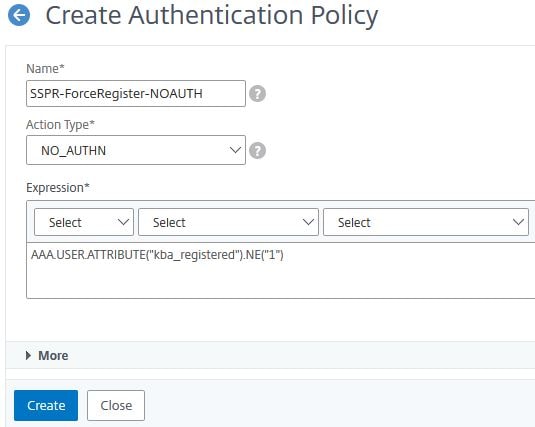
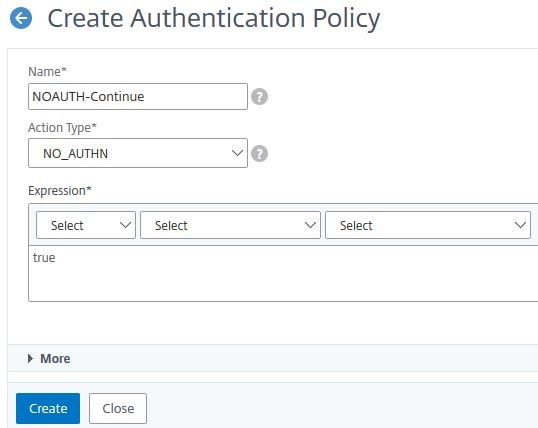
Create a third authentication policy. Enter the below information:
Name = NOAUTH-Continue
Action Type = NO_AUTHN
Expression = true
Click Create.
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> PolicyLabel -> Add.
Enter the below information:
Name = noschema-SSPR
Login Schema = LSCHEMA_INT
Click Continue.
Click Click to select.
Select SSPR-ForceRegister-NOAUTH. Click Select.
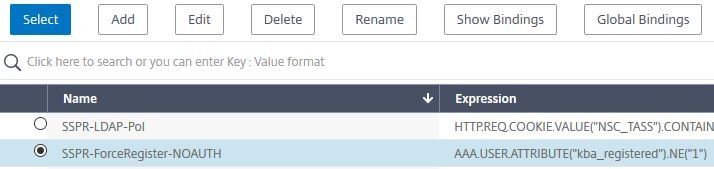
Set the Priority to 50. Under Select Next Factor, click Click to select.
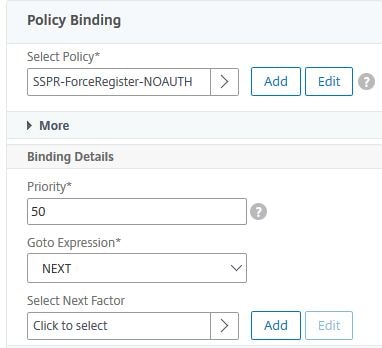
Select SSPR-PolicyLabel (created in a previous step). Click Select.
Click Bind.
Click Add Binding.
Click Click to select.
Select Authentication Policy NOAUTH-Continue. Click Select.
Set Goto Expression to END. Click Bind.
Confirm your Policy Label has authentication policies bound as below. Click Done.
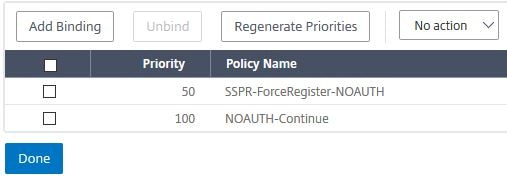
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Policy and make sure the SSPR-LDAP-Pol policy has an expression of true. It may have a different expression if you have followed on from previous steps.
Navigate to Security -> AAA – Application Traffic -> Virtual Servers and edit your AAA virtual server.
Click No Authentication Policy. If you already have an authentication policy bound, unbind it for the purpose of this demonstration.
Click Click to select.
Select LDAP_AllUsers. Click Select.
Under Select Next Factor click Click to select.
Select noschema-SSPR. Click Select.
Click Bind.
Click Done.
In this scenario, there are two users: User1, User2.
![]()
User1 has not previously registered with SSPR.
User2 has previously registered with SSPR.
If User1 attempts to connect to Gateway, during authentication, ADC detects this user has not yet registered with SSPR.
The KBA Registration page is displayed to User1.
If User2 attempts to connect to Gateway, during authentication, ADC detects this user has registered with SSPR.
User2 is passed through to Gateway.
ns.log shows that during the authentication of User2, the user has already registered with SSPR.
![]()
5. Configure SSPR password reset
With the above configuration in place that forces users to register if they have not done so already, we will build on that to add in password reset capabilities.
Scenario: Corporate user requests to reset their password. ADC validates the user by asking them to complete KBA validation and then enter an OTP code that is sent to the email address they defined during KBA validation.
Note: Email/OTP validation is optional but advised for better security.
Navigate to Security -> AAA – Application Traffic -> Login Schema -> Profiles -> Add.
Enter name SSPR-PWReset-LoginSchema. You have three pre-built password reset Login Schemas available for use:
DualAuthPasswordResetRem.xml
OnlyUsernamePasswordReset.xml
SingleAuthPasswordResetRem.xml
For the purpose of this article, we will use the SingleAuthPasswordRem.xml Login Schema. Select it from the list and click Select.
Click Create.
Click on the Policies tab and then click Add.
Enter the below information:
Name = SSPR-PWReset-LoginSchema
Profile = SSPR-PWReset-LoginSchema
Rule = true
Click Create.
Navigate to Security -> AAA – Application Traffic -> Policies – >Authentication -> Advanced Policies -> Actions -> LDAP -> Add.
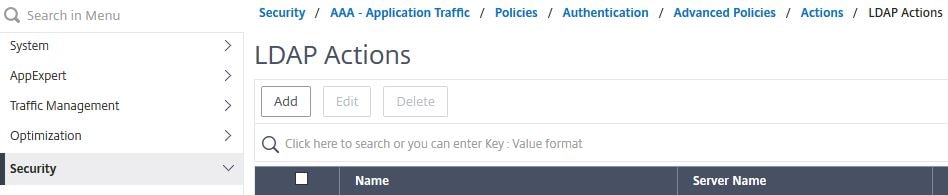
Create an LDAP server as you normally would, similar to below, only uncheck Authentication. Name the policy SSPR-Reset-AuthOff.
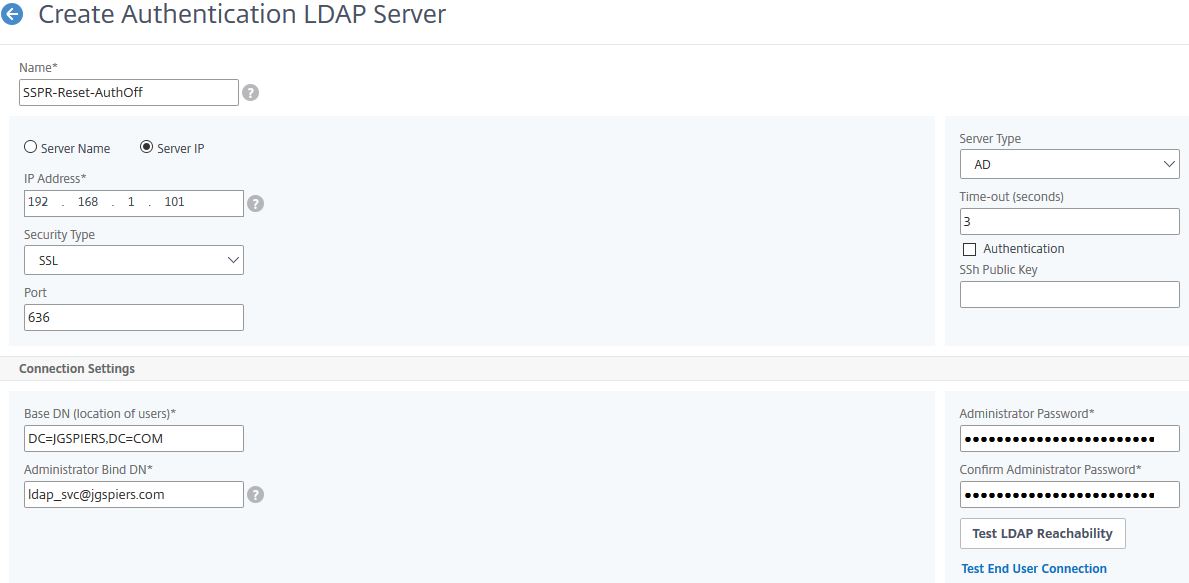
Under KB Attribute and Alternate Email enter userParameters. If you have chosen another not-in-use attribute, enter that instead. Click Create.
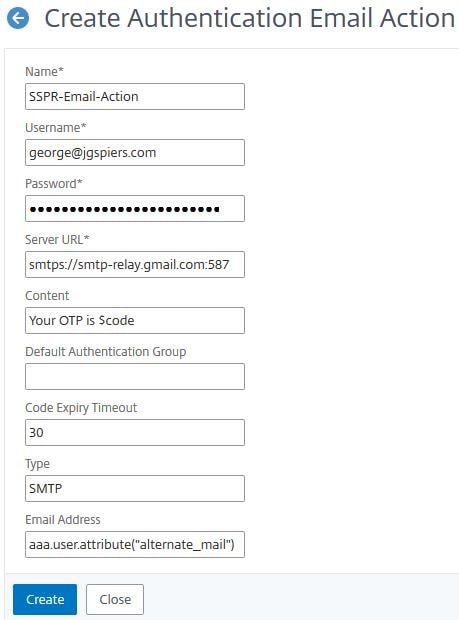
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Actions -> EMAIL -> Add.
Enter the below information:
Name = SSPR-Email-Action
Username = The email address you will send OTP emails from
Password = The password to that account, for authentication to your SMTP server
Server URL = Your SMTP server URL and port to connect on
Content = Your OTP is $code
Email Address = aaa.user.attribute(“alternate_mail”)
Click Create.
Connect to the CLI of ADC and run command add authentication policy SSPR-Email-Validation -rule true -action SSPR-Email-Action
![]()
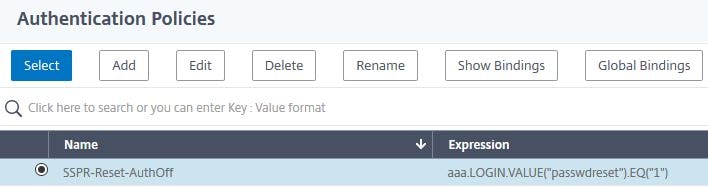
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Policy -> Add.
Enter the below information:
Name = SSPR-Reset-AuthOff
Action Type = LDAP
Action = SSPR-Reset-AuthOff
Expression = aaa.LOGIN.VALUE(“passwdreset”).EQ(“1”)
Click Create.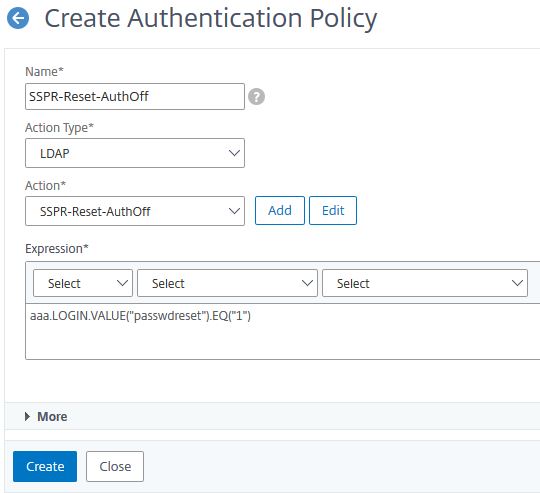
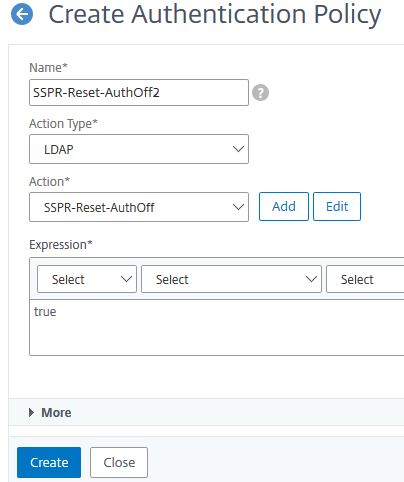
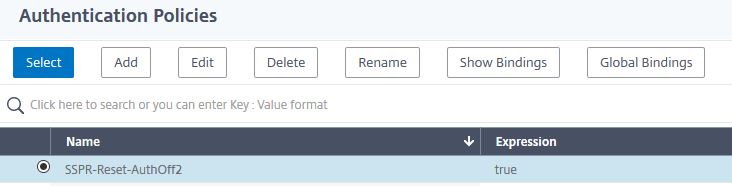
Create a second authentication policy.
Enter the below information:
Name = SSPR-Reset-AuthOff2
Action Type = LDAP
Action = SSPR-Reset-AuthOff
Expression = true
Click Create.
Navigate to Security -> AAA – Application Traffic -> Authentication -> Advanced Policies -> PolicyLabel -> Add.
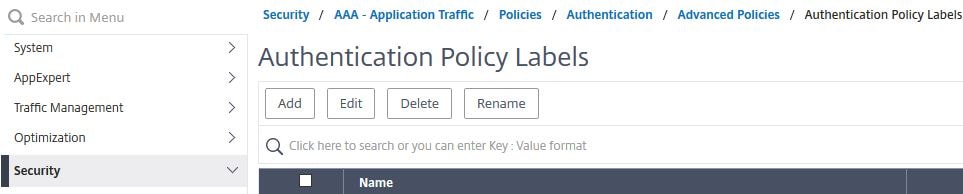
Enter the below information:
Name = SSPR-Reset-PWReset
Login Schema = LSCHEMA_INT
Click Continue.
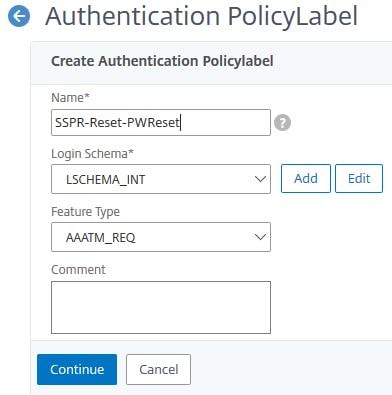
Click Click to select.
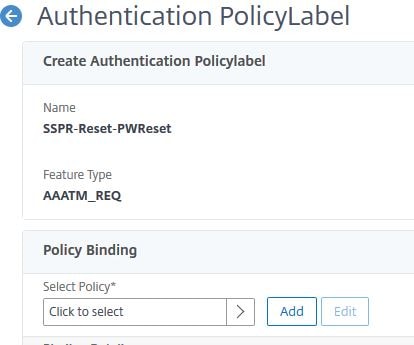
Select policy SSPR-Reset-AuthOff2, click Select.
Set Goto Expression to END. Click Bind.
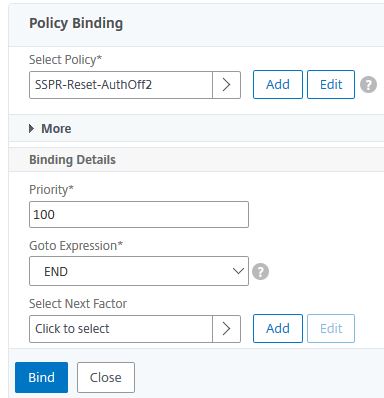
Click Done.
![]()
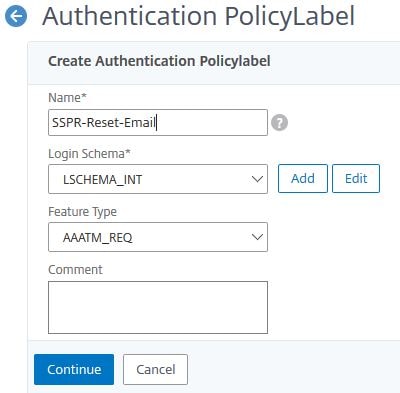
Create a second Policy Label.
Enter the below information:
- Name = SSPR-Reset-Email
- Login Schema = LSCHEMA_INT
Click Continue.
Under Select Policy, select authentication policy SSPR-Email-Validation.
Under Select Next Factor, select Policy Label SSPR-Reset-PWReset.
Click Bind.
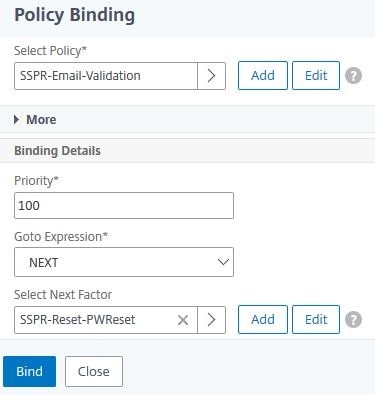
Click Done.
Create a third Policy Label.
Enter the below information:
Name = SSPR-Reset-KBA
Login Schema = LSCHEMA_INT
Click Continue.
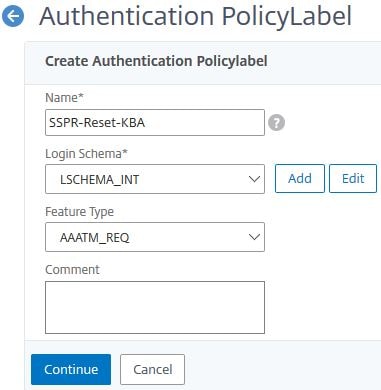
Under Select Policy, select authentication policy SSPR-Reset-AuthOff.
Under Select Next Factor, select Policy Label SSPR-Reset-Email.
Click Bind.
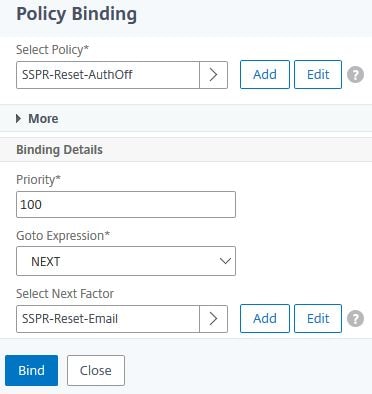
Click Done.
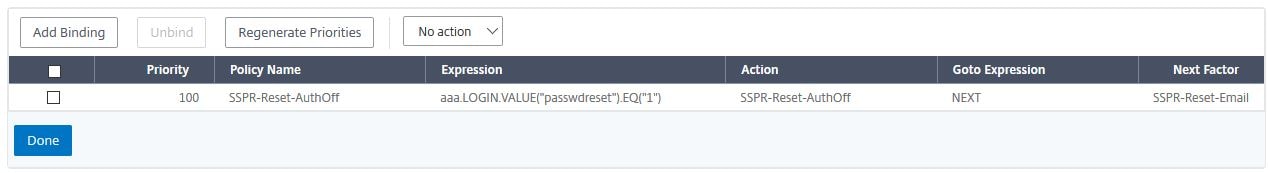
Navigate to Security -> AAA – Application Traffic -> Virtual Servers. Edit your AAA virtual server.
Click No Login Schema under Login Schemas.
Click Click to select.
Select authentication policy SSPR-PWReset-LoginSchema. Click Select.
Click Bind.
Click 1 Authentication Policy.
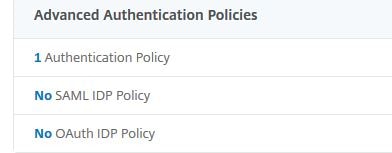
Click Add Binding.
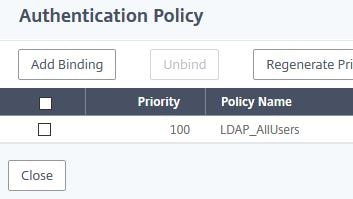
Click Click to select.
Select authentication policy SSPR-Reset-AuthOff. Click Select.
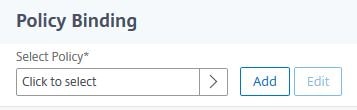
Set the Priority to 50. Click Click to select under Select Next Factor.
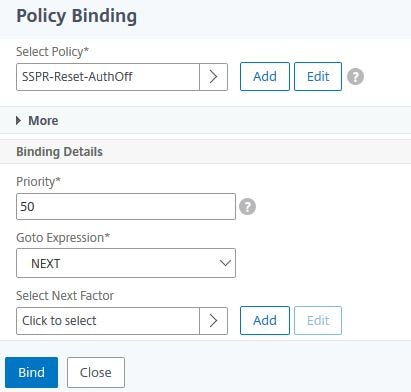
Select Policy Label SSPR-Reset-KBA. Click Select.
Click Bind.
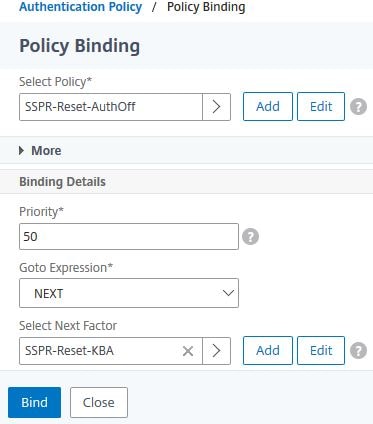
Click Close.
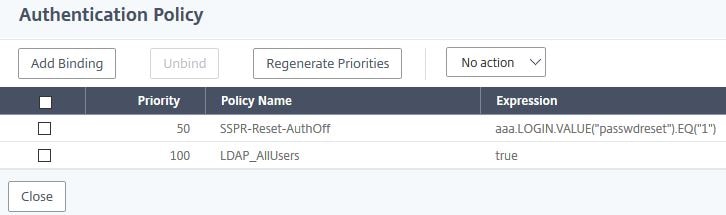
Click Done.
![]()
6. Reset password as a user
Open a web browser and navigate to your Gateway URL. Enter your user name in the User name field and click on the Forgot Password link.
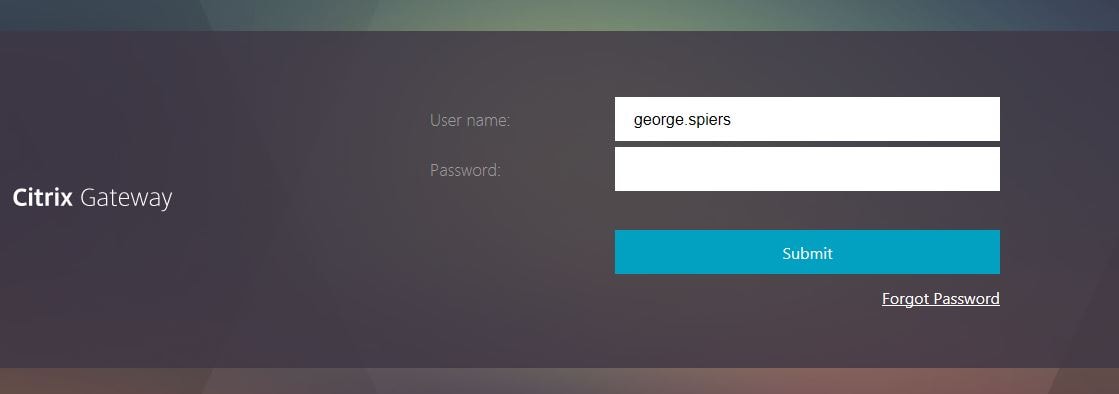
Your user name is carried through from the previous factor. Click Submit.
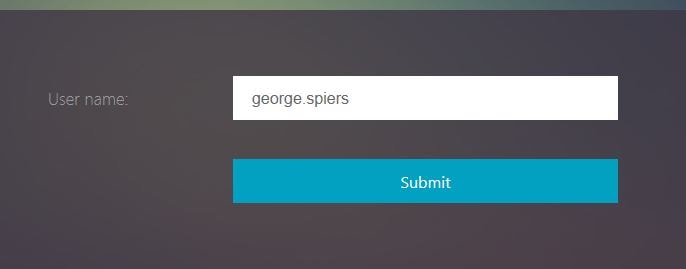
You will be challenged by two questions that you chose during KBA registration. Enter the answers and click Log On.
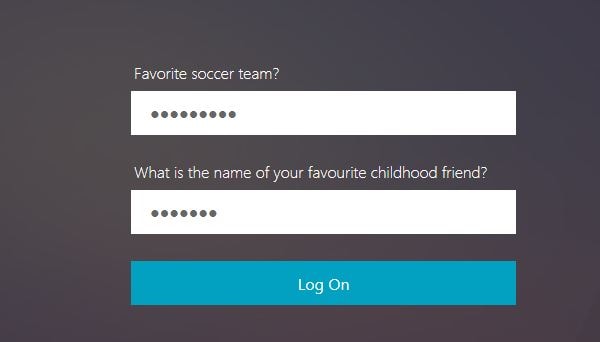
You are next challenged to enter your OTP. This will be sent to the email address you provided during KBA registration.
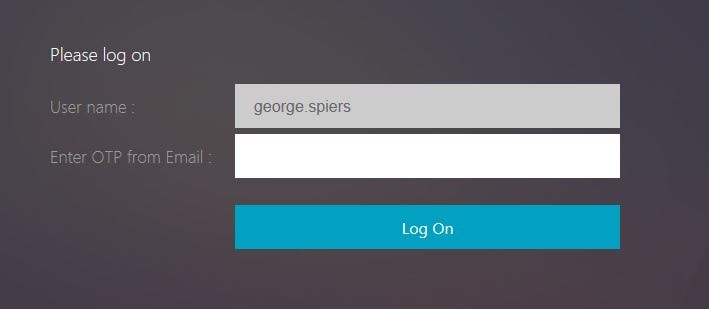
Copy the OTP code from the email you received.
Enter the OTP code into the Enter OTP from Email field. Click Log On.
If the OTP code is correct, you will be given the option to change your password. Specify a new password and click Submit.
The password reset is complete.
7. CLI commands – Force registration via attribute, and password reset with email verification -configuration
The following is assumed to be already in place:
- AAA virtual server
- AAA Authentication Profile
- Gateway virtual server
- SSPR KBA Login Schema (SSPR-Registration-Schema.xml)
add authentication loginSchema SSPR-Registration-Schema -authenticationSchema "/nsconfig/loginschema/LoginSchema/SSPR-Registration-Schema.xml"
add authentication loginSchema SSPR-PWReset-LoginSchema -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthPasswordResetRem.xml"
add authentication loginSchemaPolicy SSPR-PWReset-LoginSchema -rule true -action SSPR-PWReset-LoginSchema
add authentication ldapAction SSPR-LDAP-Pol -serverIP 192.168.1.101 -serverPort 636 -ldapBase "DC=JGSPIERS,DC=COM" -ldapBindDn ldapsvc@jgspiers.com -ldapBindDnPassword -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication ENABLED -KBAttribute userParameters -alternateEmailAttr userParameters
add authentication ldapAction SSPR-Reset-AuthOff -serverIP 192.168.1.101 -serverPort 636 -authTimeout 3 -ldapBase "DC=JGSPIERS,DC=COM" -ldapBindDn ldapsvc@jgspiers.com -ldapBindDnPassword -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -svrType AD -authentication DISABLED -KBAttribute userParameters -alternateEmailAttr userParameters
add authentication Policy SSPR-Reset-AuthOff -rule aaa.LOGIN.VALUE("passwdreset").EQ("1") -action SSPR-Reset-AuthOff
add authentication Policy SSPR-Reset-AuthOff2 -rule true -action SSPR-Reset-AuthOff
add authentication emailAction SSPR-Email-Action -userName george@jgspiers.com -password Password -serverURL "smtps://smtp-relay.gmail.com:587" -content "Your OTP is $code" -timeout 30 -type SMTP -emailAddress aaa.user.attribute("alternate_mail")
add authentication policy SSPR-Email-Validation -rule true -action SSPR-Email-Action
add authentication policylabel SSPR-Reset-KBA -loginSchema LSCHEMA_INT
add authentication Policy LDAP_AllUsers -rule true -action SSPR-LDAP-Pol
add authentication Policy SSPR-LDAP-Pol -rule true -action SSPR-LDAP-Pol
add authentication Policy SSPR-ForceRegister-NOAUTH -rule "AAA.USER.ATTRIBUTE(\"kba_registered\").NE(\"1\")" -action NO_AUTHN
add authentication Policy NOAUTH-Continue -rule true -action NO_AUTHN
add authentication policylabel noschema-SSPR -loginSchema LSCHEMA_INT
add authentication policylabel SSPR-PolicyLabel -loginSchema SSPR-Registration-Schema
add authentication policylabel SSPR-Reset-PWReset -loginSchema LSCHEMA_INT
add authentication policylabel SSPR-Reset-Email -loginSchema LSCHEMA_INT
bind vpn global -userDataEncryptionKey unifiedgateway.jgspiers.com
bind authentication policylabel SSPR-PolicyLabel -policyName SSPR-LDAP-Pol -priority 100 -gotoPriorityExpression END
bind authentication policylabel noschema-SSPR -policyName SSPR-ForceRegister-NOAUTH -priority 50 -gotoPriorityExpression NEXT -nextFactor SSPR-PolicyLabel
bind authentication policylabel noschema-SSPR -policyName NOAUTH-Continue -priority 100 -gotoPriorityExpression END
bind authentication vserver AAA-vServer -policy LDAP_AllUsers -priority 100 -nextFactor noschema-SSPR -gotoPriorityExpression NEXT
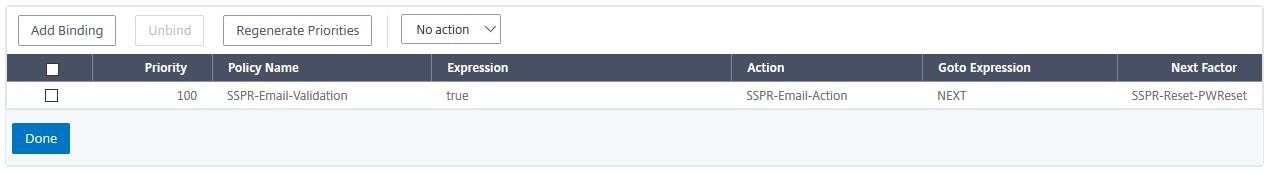
bind authentication policylabel SSPR-Reset-PWReset -policyName SSPR-Reset-AuthOff2 -priority 100 -gotoPriorityExpression END
bind authentication policylabel SSPR-Reset-Email -policyName SSPR-Email-Validation -priority 100 -gotoPriorityExpression NEXT -nextFactor SSPR-Reset-PWReset
bind authentication policylabel SSPR-Reset-KBA -policyName SSPR-Reset-AuthOff -priority 100 -gotoPriorityExpression NEXT -nextFactor SSPR-Reset-Email
bind authentication vserver AAA-vServer -policy SSPR-PWReset-LoginSchema -priority 100
bind authentication vserver AAA-vServer -policy SSPR-Reset-AuthOff -priority 50 -nextFactor SSPR-Reset-KBA -gotoPriorityExpression NEXT8. CLI commands – Force registration via attribute, and password reset without email verification -configuration
The following is assumed to be already in place:
- AAA virtual server
- AAA Authentication Profile
- Gateway virtual server
- SSPR KBA Login Schema (SSPR-Registration-Schema.xml)
add authentication loginSchema SSPR-Registration-Schema -authenticationSchema "/nsconfig/loginschema/LoginSchema/SSPR-Registration-Schema.xml"
add authentication loginSchema SSPR-PWReset-LoginSchema -authenticationSchema "/nsconfig/loginschema/LoginSchema/SingleAuthPasswordResetRem.xml"
add authentication loginSchemaPolicy SSPR-PWReset-LoginSchema -rule true -action SSPR-PWReset-LoginSchema
add authentication ldapAction SSPR-LDAP-Pol -serverIP 192.168.1.101 -serverPort 636 -ldapBase "DC=JGSPIERS,DC=COM" -ldapBindDn ldapsvc@jgspiers.com -ldapBindDnPassword -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -authentication ENABLED -KBAttribute userParameters -alternateEmailAttr userParameters
add authentication ldapAction SSPR-Reset-AuthOff -serverIP 192.168.1.101 -serverPort 636 -authTimeout 3 -ldapBase "DC=JGSPIERS,DC=COM" -ldapBindDn ldapsvc@jgspiers.com -ldapBindDnPassword -ldapLoginName sAMAccountName -groupAttrName memberOf -subAttributeName cn -secType SSL -svrType AD -authentication DISABLED -KBAttribute userParameters -alternateEmailAttr userParameters
add authentication Policy SSPR-Reset-AuthOff -rule aaa.LOGIN.VALUE("passwdreset").EQ("1") -action SSPR-Reset-AuthOff
add authentication Policy SSPR-Reset-AuthOff2 -rule true -action SSPR-Reset-AuthOff
add authentication policylabel SSPR-Reset-KBA -loginSchema LSCHEMA_INT
add authentication Policy LDAP_AllUsers -rule true -action SSPR-LDAP-Pol
add authentication Policy SSPR-LDAP-Pol -rule true -action SSPR-LDAP-Pol
add authentication Policy SSPR-ForceRegister-NOAUTH -rule "AAA.USER.ATTRIBUTE(\"kba_registered\").NE(\"1\")" -action NO_AUTHN
add authentication Policy NOAUTH-Continue -rule true -action NO_AUTHN
add authentication policylabel noschema-SSPR -loginSchema LSCHEMA_INT
add authentication policylabel SSPR-PolicyLabel -loginSchema SSPR-Registration-Schema
add authentication policylabel SSPR-Reset-PWReset -loginSchema LSCHEMA_INT
bind vpn global -userDataEncryptionKey unifiedgateway.jgspiers.com
bind authentication policylabel SSPR-PolicyLabel -policyName SSPR-LDAP-Pol -priority 100 -gotoPriorityExpression END
bind authentication policylabel noschema-SSPR -policyName SSPR-ForceRegister-NOAUTH -priority 50 -gotoPriorityExpression NEXT -nextFactor SSPR-PolicyLabel
bind authentication policylabel noschema-SSPR -policyName NOAUTH-Continue -priority 100 -gotoPriorityExpression END
bind authentication vserver AAA-vServer -policy LDAP_AllUsers -priority 100 -nextFactor noschema-SSPR -gotoPriorityExpression NEXT
bind authentication policylabel SSPR-Reset-PWReset -policyName SSPR-Reset-AuthOff2 -priority 100 -gotoPriorityExpression END
bind authentication policylabel SSPR-Reset-KBA -policyName SSPR-Reset-AuthOff -priority 100 -gotoPriorityExpression NEXT -nextFactor SSPR-Reset-PWReset
bind authentication vserver AAA-vServer -policy SSPR-PWReset-LoginSchema -priority 100
bind authentication vserver AAA-vServer -policy SSPR-Reset-AuthOff -priority 50 -nextFactor SSPR-Reset-KBA -gotoPriorityExpression NEXT
Carl Stalhood
January 24, 2019Hi George, are you able to attach the full list of CLI commands that you used to configure this feature? Thanks.
George Spiers
January 24, 2019Hi Carl, see section 7.
Carl Stalhood
January 24, 2019Perfect. Thanks.
Victor Fuenmayor
January 28, 2019George, do you have the BUG ID for BUG mentioned in Section 2?
“There is a current bug in the 12.1.50.28 firmware that does not allow a larger key size to be used with SSPR.”
I need to find out when this is fixed.
George Spiers
January 29, 2019The release notes of 50.31 has this bug mentioned and below the bug appears “NSAUTH-5342”. Don’t think that is of any use. There is no actual bug number listed. I was told it would be fixed in February.
Pingback: EUC Weekly Digest – February 2, 2019 – Carl Stalhood
Steve Haugh
March 5, 2019Hi George, Can you run SSPR with the OTP for 2FA function on the NS?
George Spiers
March 7, 2019Sure you can, just make sure that OTP and SSPR use different AD attributes.
Sean
December 22, 2021Hello George,
I know this an old post, but I would really appreciate if you can show us how to implement sspr and 2fa. I have contacted Citrix on multiple occasions regarding this implementation and they all tell me it cannot be done. Can you please proof them wrong.
Best,
Sean
Pingback: nFactor Authentication – NetScaler Gateway 12 / Citrix Gateway 12.1 – Carl Stalhood
John Carmody
March 22, 2019Hi George i get to the step 6 put my user name in and click forget password and confirm username. I get then asked the security questions which i complete but after clicking on logon i then get a cannot complete your request error and can go no further
“You are next challenged to enter your OTP. This will be sent to the email address you provided during KBA registration” <<< I dont get this i get the cannot complete your request error
i have checked the delivery services log on my storefront server and no errors in there any ideas?
George Spiers
March 24, 2019I would just double check your authentication policy and Login Schema bindings to make sure they are correct. Also, upgrade to at least build 12.1.51.16, and make sure you have ran command “bind vpn global -userDataEncryptionKey yourcertname” without the quotation marks. You can also enable syslog debugging on ADC and check those for any hints.
Leanid
March 27, 2019I am trying to make it work for Citrix XenApp. I have working Gateway configuration for XenApp Virtual Server. I have upgraded Netscaler to 12.1.51.16.nc
When I remove basic authentication and add Authentication profile all requests to my sites get redirected to this URL: https://mysite.com/logon/LogonPoint/tmindex.html (before I had https://mysite.com/vpn/index.html)
even if I type https://mysite.com/register it get redirected to above URL /logon/LogonPoint/tmindex.html. And entering user credential just shows error: “No Active policy during authentication”.
What am I missing?
George Spiers
April 2, 2019No active policy normally means you either have no authentication policy bound to your AAA vServer, or the expression used is incorrect and is not evaluating to true.
Sunny
March 29, 2019Great Articles, thanks very much, George!
Need some clarifications:
Does “external users” refer to domain users accessing StoreFront published app over the Internet via NetScaler Gateway?
If yes,
Do we need to setup both SSPR for NetScaler and SSPR for VirtualApp to allow “external users” to reset password over the Internet?
If no,
Which SSPR should we setup to enable this function for these users? SSPR for NetScaler or SSPR for VirtualApp?
George Spiers
April 2, 2019SSPR for NetScaler is what you need for remote users. It is also possible for internal users to route to the same Gateway and use the same SSPR, but some organisations place the Gateway in DMZ and do not allow such internal routing, in which case SSPR for Virtual Apps and Desktops is required.
Anonymous
April 2, 2019Thanks so much, George!
Our NetScaler Gateway is located in the DMZ. Thus, we will give SSPR for Virtual Apps and Desktops a go. Really appreciate your comment!
Sunny Ko
April 2, 2019Thanks so much, George!
Our NetScaler Gateway is located in the DMZ. Thus, we will give SSPR for Virtual Apps and Desktops a go. Really appreciate your comment!
Leanid
April 8, 2019I have manage to implement nFactor. I used Stan Demburg (https://www.irangers.com/netscaler-native-otp-limit-enrollment-one-device) approach. Modified it a bit to add OTP to /manageOTP (for users with registered devices). I used your article to add KBA password reset (I also protected it with OTP). nFactor works fine. It did get a bit complicated.
At my login page I have 3 extra link one /manageotp, /register and “Forgot password”.
But main problem is NSC_TASS cookie.
I actually have 2 problem with it.
Problem 1) When user login to main site (StoreFront) and logoff. It presented with Logon button. When user click on it NSC_TASS cookie get set to NSC_TASS=/Citrix/MyStoreFront/login.aspx
Now if I click any of my links /manageotp, /register not working. Since NSC_TASS is not getting reset to manageotp or /register. Browser restart needed.
Problem 2) When user restart browser he can get into /manageotp or /register. Cookie get set NSC_TASS=/register. But if user decided to abandon this registration he gets stuck. No Cancel button, no NSC_TASS cookie reset. Only way out is re-start Browser. This is bad user experience and probably support call.
I am probably looking for 2 solutions. I hope someone have implemented it already.
1) Modify /register /manageotp and if possible “Forgot Password” links to make sure NSC_TASS properly set or old one cleared. I guess some custom java script needed for it.
2) Provide “Cancel” button to each nFactor Login schema. That can reset cookie. Similar like “Log off” button does at /manageotp page.
Or any other solutions to clear NSC_TASS so user don’t get stuck in nFactor and have to restart Browser. I have feeling if I go live with current cookie issue our support will go crazy trying telling clients to restart browsers.
Leanid
April 15, 2019I have resolved my NSC_TASS cookie issue with multiple solutions.
1) Added global responder policy to reset NSC_TSCC cookie when referrer is StoreFront. This allows me to go back to manageotp or /register after user logoff from StoreFront.
2) Added Cancel button to all nFactor auth forms This was a bit difficult. Had to make custom button with java scripts. In short I had to add element of input type=submit with action /nf/auth/doLogoff.do to cancel default submit form action.
And added cookie NSC_TASS_CLEAR=yes when this button is clicked.
3) Then at netscaler global responder policy I capture this NSC_TASS_CLEAR cookie and reset NSC_TASS. I had to do this because original NSC_TASS cookie has HttpOnly flag and is not available for javascript manipulations.
4) Added some css to make Cancel button look flat.
neztik
June 11, 2019Leanid,
We are running into the same issue. Any chance you could share your code changes?
Leanid
June 11, 2019Can’t post for some reason. It shows 404 when I try.
Leanid
June 11, 2019Try this link. I will keep this file for a while
https://drive.google.com/file/d/1BCJHKXxEtWEJj9bWVYuXo0ZIEpVyMfq7/view?usp=sharing
Morten Kallesøe
May 14, 2019I think there is a inconsistency with the attribute field you have configured(userParameters) and the one in your no_authn policy(kba_registered)
i’ve not doubled checked it, but from the looks of it, it wont work, unless magic is going on.
George Spiers
May 16, 2019No, that is normal. kba_registered is simply an AAA attribute.
Morten
May 17, 2019And this KEY/VALUE(AAA.USER.ATTRIBUTE(“kba_registered”) gets a value based on the information retrieved on the LDAP Action? it makes sense, but for the visbile eye its hard to see.
George Spiers
May 17, 2019kba_registered is an internal attribute (in ADC) that the ADC uses to check if a user is registered or not.
Z Sheikh
May 16, 2019Great Article, thanks very much, George!
Do you know if its possible to have SSPR work without an alternate email or to restrict the alternate email to a specific domain?
Anonymous
May 16, 2019hey Z.
you dont need to use alternate email, and i would believe that restricting the domain is possible.
Zishan Sheikh
May 16, 2019If alternate email is not used is the option to change password simply provided after answering the questions correctly?
George Spiers
May 16, 2019Yes correct.
Tiago
May 20, 2019George, is it also possible to unlock account like we can do via Self-Service Password Reset (on-prem with Storefront)?
George Spiers
May 27, 2019No this is strictly only for password resets.
Pingback: nFactor Authentication – Citrix Gateway 13 – Carl Stalhood
Duncan
June 11, 2019Hi George, Great Article, just a question on top of Zishan’s question do you still setup the same way if you werent using the alternate email option
George Spiers
June 16, 2019Yes, just leaving out the email verification/regsitration parts.
Duncan Brown
June 19, 2019Hi George
I tried that but it now just goes straight through to resetting password without answering security questions which is a bit of a worry. What am i missing !!!
thanks
George Spiers
June 20, 2019Create a new Login Schema but leave “Register Alternate Email” unchecked. Register a new user and make sure it doesn’t ask you for an Alternate Email Id. Once registration is complete, verify the userParameters AD attribute is populated. Don’t bind an EMAIL action/policy to the AAA vServer. Do not create the SSPR-Reset-Email Policy Label.
Anonymous
June 20, 2019Hi George
Ok so can i just clarify if i dont do the EMail policy label, then what do i do with the third policy (SSPR-Reset-KBA) label when the next factor is SSPR-Reset-Email, do i simply not add that policy either.
Also i am noticing on the Netscaler VM itself it is registering “bind_vipconfig: got bind for SSPR-PWReset-LoginSchema” but didnt find it in the global list.
appreciate you help with this George, thanks
George Spiers
June 21, 2019Hi – Add SSPR-Reset-KBA Policy Label but don’t select a Next Factor, just bind the “SSPR-Reset-AuthOff” policy to it.
Duncan Brown
June 24, 2019Hi George
i tried that as well and it still does the same thing just goes straight through to inputting new password without answering questions from KBA. i did notice on Citrix Office information as below it says you must provide an Alternate email. does that mean you need to use the Alternate Email. have you ever set it up without the Alternate email ?
thanks – Duncan
New user self-registration. You can self-register as a new user.
Configure knowledge-based questions. As an administrator, you can configure a set of questions for users.
Alternate email ID registration. You must provide an alternate email ID while registration. The OTP is sent to the alternate email ID because the user has forgotten the primary email ID password.
Duncan Brown
June 24, 2019Hi George
unfortunatley it still does the same thing go straight through to change password and it bypasses answering the Security Questions. Are you sure you can do it without alternative email as on Citrix Documentation is states :
Alternate email ID registration. You must provide an alternate email ID while registration. The OTP is sent to the alternate email ID because the user has forgotten the primary email ID password.
and
The Citrix ADC knowledge-based question and answer, and email OTP uses AD attribute to store users data. You must configure an AD attribute to store the questions and answers along with the alternate email ID.
thanks
Duncan
George Spiers
June 25, 2019I’ve not set it up without email registration but it should work. I’ll try it and post the config.
Anonymous
June 26, 2019Hi George
Did you have any luck?
thanks
Duncan
George Spiers
June 27, 2019Sorry have not had a chance yet – should get something to you by Monday.
George Spiers
June 30, 2019OK – so you need to:
1. create a new “KBA Registration” Login Schema with “Regsiter Alternate Email” unchecked.
2. edit the existing “SSPR-Registration-Schema” Login Schema Profile and choose the new Authentication Schema you just created.
3. edit the “SSPR-Reset-KBA” Policy Label and unbind the existing from it.
4. bind “SSPR-Reset-AuthOff” to the SSPR-Reset-KBA Policy Label. Set Next Factor to “SSPR-Reset-PWReset”.
That is a confirmed working configuration. If it is still not working for you something in your configuration is incorrect and I suggest using a test VPX issuing all the CLI commands at the bottom of this article so that you have a working configuration, and then perfom the steps above.
Duncan Brown
July 2, 2019Hi George
I am afraid to say it still doesnt work and i have followed your instructions to the T. would it be cheeky to ask you to create a CLI command list specifically for the No Email registration from your working config you have to see if we can replicate it that way,
appreciate your assistance with this.
thanks
Duncan
George Spiers
July 3, 2019Yep – I’ll get the CLI config posted later today.
Anthony
December 14, 2020Hi George
Im having issue on registering on KBA it saying cannot complete request do you have any input on this error?
Moshe Ben Dahan
June 30, 2019Hi George,
First a great guide i’m really appreciating.
The configured is only the KBA reset with no email.
I’ve observed the following log:
Null password check failed in ldap authentication: 1
while clicking on the forget password and entering only the username and submit.
Do i miss something ?
Thanks
Moshe
George Spiers
July 3, 2019Hello. When you enter the username and click submit, what error message do you get? You are not receiving the KBA questions?
fawzy
July 1, 2019Also with KBA reset and no email. I got this error after changing password “Password change failed. Make sure you supply correct existing password and try again.”
George Spiers
July 3, 2019I’ll get the CLI commands posted for config without email so you can replicate it in your lab.
Duncan Brown
July 14, 2019Hi George
would just like to say thank you very much for your help on this. It is now working as expected. Much appreciated thanks
Duncan
George Spiers
July 14, 2019Cool. Glad to hear it.
Trevor
July 12, 2019Thanks again for another great article. I have a opinion question. I just demo’d to a customer SSPR who has on the average 2400 password reset support calls so they liked what I presented. However, the security guy stated “no corporation out there puts a link on the external site to reset passwords”. Keep in mind they already use ADC with 2FA. It was an interesting comment, so I pose to you this question, “in your experience what companies have put this into play, large enterprise, small business, financial institutions?” Curious.
George Spiers
July 14, 2019Can’t comment on what companies have deployed this feature. However, I can reset my password from Azure AD and the Office 365 portal which is externally accessible. The ADC reset password portal can be easily protected by 2FA, and the security questions + email verification are additional factors.
William
July 24, 2019Is there no way you can get this to lock or limit the number of attempts at guessing the security questions?
Implemented in this way with no incorrect usage limits, it is against OWASP guidelines (OTG-AUTHN-008) and cannot be implemented if it shares a DMZ with any PCI environment.
This seems like a huge oversight on Citrix’s part.
Sunny
July 24, 2019FYI.
ADC SSPR’s Alternate email option does not work with ADC 12.1 build 52.15 with Enterprise license. Platinum license is currently required. We ran into this problem in our test.
Citrix Support/Product’s response is this should be corrected in ADC 12.1 build 52.16 in the future to work with Enterprise license. No ETA though.
George Spiers
July 26, 2019Thanks for the information.
Philipp Zenz
August 13, 2019Hi guys,
is it possible to only use the alternate email without the questions?
I could´t create an Login Schehma without questions.
kind regards
Philipp
George Spiers
August 19, 2019No not yet. Citrix are working on providing this capability.
Lim
August 20, 2019Hi George,
Great Article. Really appreciate your guidance on configuring SSPR.
Actually I am currently testing on configuring SSPR on a separate Auth vserver, means I have an IP that is going to a AAA vserver only for the purpose to do SSPR.
I can see from your steps involves running the SSPR on the Citrix Gateway, however is it possible to enable SSPR on AAA vserver?
Regards,
Lim
George Spiers
August 26, 2019Yes AAA is the virtual server that handles SSPR, your LB virtual servers can use it, or Gateway.
Pinkesh Patel
November 1, 2019Hey George, This might resolve some authentication issues we are having. However, i want to present our scenario.
– A user outside of the network needs to change their initial password because it is their very first time logging into the domain. This requires the user to change their temporary password. If this is the case, then what happens after they enter their initial temporary password? Will they be prompted to change their password first then go to the KBA registration? Or will they enter their temp password then directly go into KBA registration, then the screen to set their password?
—-
We have an issue where the user logs in with a temp password, they change the password on first login to the storefront, but then the DDC authenticates to a secondary domain controller that hasn’t seen the replication from the password change from the first domain controller. I was hoping the authentication from storefront then DDC would go to the same Domain controller but it seems like it’s just picking a random DC.
Thanks!!
George Spiers
November 17, 2019I haven’t tested that scenario to be honest. It will either allow the user to change their password first, or else ask the user to register with SSPR first. Otherwise, you could disable SSPR registration enforcement.
How have you configured Password Validation?
Anonymous
November 18, 2019I’ve been looking into the XML-based password vailidation but i can’t find out how the XML database populating with the usernames and passwords. It really depends on how often and quick AD replicates to the XML service. That’s if our AD replications to the XML service. If it’s instant then it might work for us.
Pinkesh Patel
November 1, 2019Hey George, This might resolve some authentication issues we are having. However, i want to present our scenario.
– A user outside of the network needs to change their initial password because it is their very first time logging into the domain. This requires the user to change their temporary password. If this is the case, then what happens after they enter their initial temporary password? Will they be prompted to change their password first then go to the KBA registration? Or will they enter their temp password then directly go into KBA registration, then the screen to set their password?
—-
We have an issue where the user logs in with a temp password, they change the password on first login to the storefront, but then the DDC authenticates to a secondary domain controller that hasn’t seen the replication from the password change from the first domain controller. I was hoping the authentication from storefront then DDC would go to the same Domain controller but it seems like it’s just picking a random DC.
Thanks!!
-trying to post again cause i dont see my original post. sorry for duplicates.
Leanid
August 4, 2020George,
As usual excellent write up. I used your multiple recipes to implement MFA and KBA. After few weeks I think I got where I want it.
I think I also manage to implement KBA secure enough for external password Reset. I did couple of changes to your flow.
My KBA implementation:
KBA subscription (on different AAA site with Cancel button to redirect to main). If user registred for OTP it is protected by OTP as well.
Password Reset:
1) click “forgot Password”
2) Ask user name and solve “Google Captcha” as per your article: https://jgspiers.com/citrix-adc-nfactor-authentication-google-recaptcha-first-ldap-second-factor/
3) Ask Email OTP. I had to move it around, since Netscaler KBA is not limiting how many times you can try to answer KBA. I felt it is more secure to get email OTP before showing KBA factor
4) Ask KBA
5) Go to password Reset
Also for OTP registration for main portal I have configured separate AAA and set it up for /manageotp cookie, with cancel button to go to main site. If user already enrolled in OTP it will ask OTP factor before going to /manageotp to add/remove devices.
Had to do couple of changes here and there. For example with new Netscaler 13.X you don’t need anymore custom script for Google Captcha. It is already implemented and it takes secret from configuration settings.
To add Cancel button I used custom function (works to go from secondary AAA site to main Gateway site or cancel OTP on main site as well, does not reset cookie):
CTXS.ExtensionAPI.addCustomCredentialHandler({
getCredentialTypeName: function () { return “nsg_cancel”; },
getCredentialTypeMarkup: function (requirements) {
var div = $(“”);
$(document).on(‘ctxsformsauthenticationdisplayform’, function (e, data) {
$(‘#nsg_cancel’).click(function() {
CTXS.Events.publish(CTXS.Events.gateway.sessionTerminated);
window.location.href = “https://mainportal.site.com/”; //change that
})
});
return div;
}
});
Pingback: Citrix Password Reset Portal - Find Official Portal
Muso
June 7, 2021I want to reset my password. I am now blocke
Sean
August 4, 2021Hi George,
I know this post is a couple of years old, but my company is just trying to implement SSPR, and the only thing I’m worry about is 2FA. Can SSPR be configured and still have 2FA active on the same gateway?
Thank you,
Seam
Rafal
September 6, 2021Hello,
have You got this kind of error after entering answers for reset password? I am able successfully register KBA questions in AD, but looks like NS has some issues with reading them?
“KBA Validation: State Context verification failed”
Regards
Rafal
darrin
July 26, 2022Morning all,
is there a way to specify 3 questions/prompts ?
We want to force SSPR to use 3 questions not just 2 to confirm user.
franky
December 5, 2022Hi there,
I follow the step in here to create KBA registration, however, during submitting the answer for registering to userParameters (AD attribute),:
1. it didnt register to the attribute.
2. the KBA registration upon submit, provide an error “Cannot complete your request.” and looping back to the question again
3. Google capture showing showing Http/1.1 Internal Server Error 43531 upon submitting
Any got an idea ??
sharif
August 18, 2023Hi All,
I have followed the article. Everything works fine except the user is able to reset the same password again. I have changed on the Active Directory ” Enforce password history” and ” Minimum password age ” but that did not solve the use.
Anyone got an idea