Native one time password using Citrix NetScaler is a new feature released in version 12.0 build 51.24. Using the native OTP capabilities of NetScaler reduces the need to purchase third party authentication systems when you want to protect your resources with multiple factors of authentication. Alternatively you could use OTP for certain users and the remaining users receive a different OTP solution that has extra functionality such as push-notifications.
Native OTP is built on the nFactor authentication system which requires an AAA Virtual Server and advanced authentication policies. I have described nFactor in detail including it’s capability across the following posts:
https://jgspiers.com/single-sign-on-office-365-netscaler-saml-azure-mfa-authentication/
https://jgspiers.com/netscaler-nfactor-authentication-google-recaptcha-first-ldap-second-factor/
https://jgspiers.com/nfactor-authentication-with-netscaler-gateway/
Requirements:
- Because we need to use nFactor, you’ll require a NetScaler Enterprise license at a minimum.
- An Active Directory Domain Functional Level of 2008 and above is also supported.
- A NetScaler bind account with permissions to manage the userParameters Active Directory attribute for enrolling users.
The following guide describes setting up a one-time password portal where users enrol their mobile devices and manage their enrolled devices going forward. NetScaler Gateway will also be used to protect XenDesktop resources by challenging users for their LDAP credentials and a one-time password. The mobile app used to provide the one-time password is Google Authenticator. Keep in mind that any application that supports one time passwords can be used, such as Microsoft Authenticator.
♣ Create AAA vServer
♣ Create Authentication Policies
♣ Create Login Schemas
♣ Create Policy Label
♣ Create Traffic Policy
♣ Bind Login Schemas to AAA vServer
♣ Bind Authentication Policies to AAA vServer
♣ Enrol Mobile Phones for One-Time Password
♣ Test One-Time Password Authentication
♣ Additional Thoughts & Troubleshooting
Create AAA vServer
Create an Authentication virtual server. An IP is not needed so set the IP Address Type to Non Addressable. Click OK.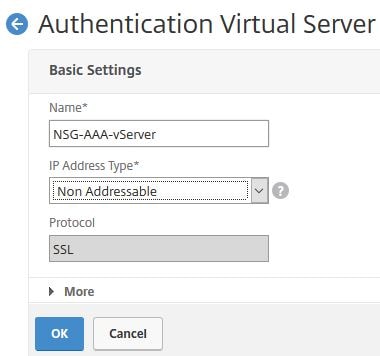
Bind any server certificate to the virtual server. It does not matter which one. 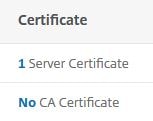
Make sure the Portal Theme is set to RfWebUI. Click OK -> Done. 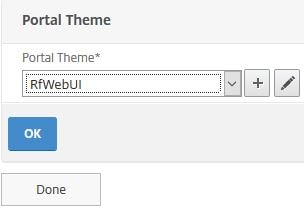
Next create an Authentication Profile and under Authentication Host enter any URL, it does not matter. Under Authentication Virtual Server select the AAA vServer you just created. Click Create.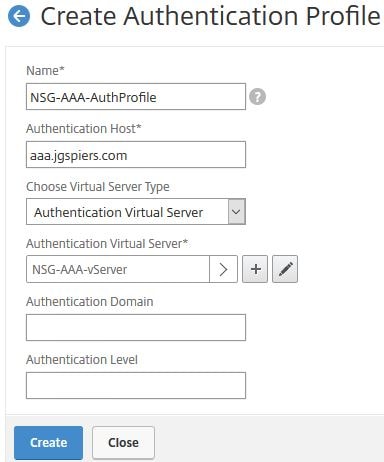
Edit your NetScaler Gateway virtual server and under Authentication Profile choose the profile you just created. No basic authentication policies should be attached to the NetScaler Gateway vServer. Click OK.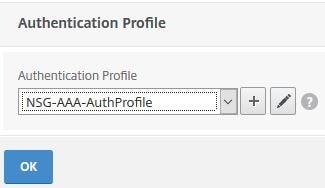
Create Authentication Policies
Next we will create the required advanced Authentication Actions/Profiles, Policies, Login Schemas and Policy Labels. Firstly navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Actions -> LDAP -> Add.
The first LDAP server action will be for standard LDAP authentication. Enter a name, the LDAP IP and bind account information.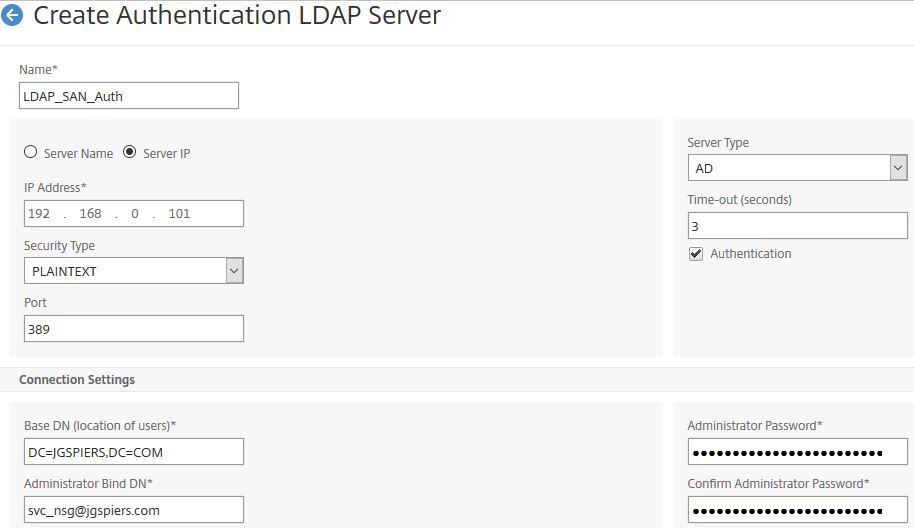
Under Server Logon Name Attribute enter sAMAccountName. Under Group Attribute enter memberOf if you want to perform LDAP group extraction and under SSO Name Attribute enter cn. Click Create. 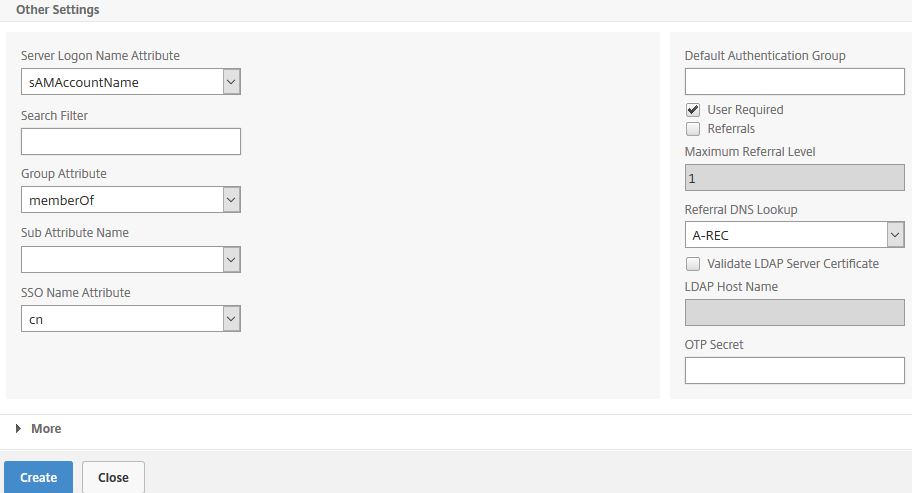
Create a second LDAP action, this time for OTP Management authentication. Uncheck Authentication and enter other details as below.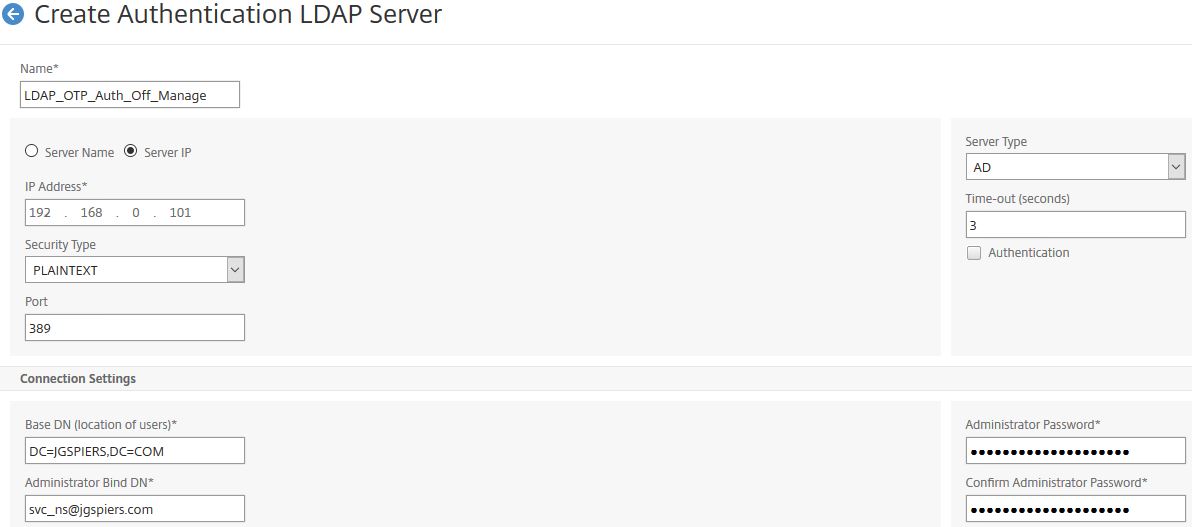
Under OTP Secret enter userParameters and click Create.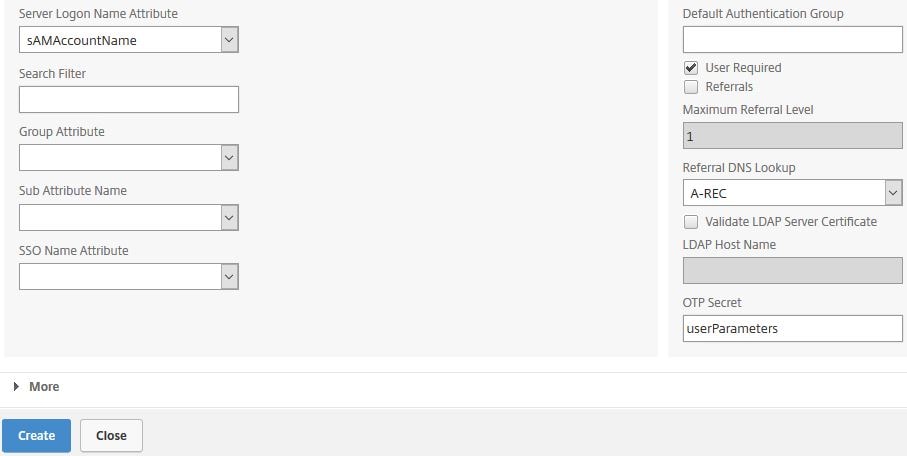
Create a third LDAP Authentication action for OTP Challenge authentication. Uncheck Authentication as with the above policy but this time under Search Filter enter userParameters>=#@. I discovered an issue were the OTP Challenge which is obviously going to be internet facing was allowing users to log on with single factor LDAP authentication if that user had not yet enrolled any device. Even though the Login Schema presented users with an OTP Passcode field and LDAP username/password fields, users did not have to enter anything in the OTP Passcode field if they had not enrolled a device. This is because the last factor in the chain has authentication disabled meaning Group Extraction is simply performed rather than verifying username and password. The Search Filter will now make sure a user has enrolled their device with OTP and if not, they cannot log on using LDAP+OTP until they enrol.
Navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Authentication Policies -> Add.
Enter a name for the OTP LDAP Management policy. Under Action select the LDAP SAN action. Enter an expression of HTTP.REQ.COOKIE.VALUE(“NSC_TASS).EQ(“manageotp”) and click Create. 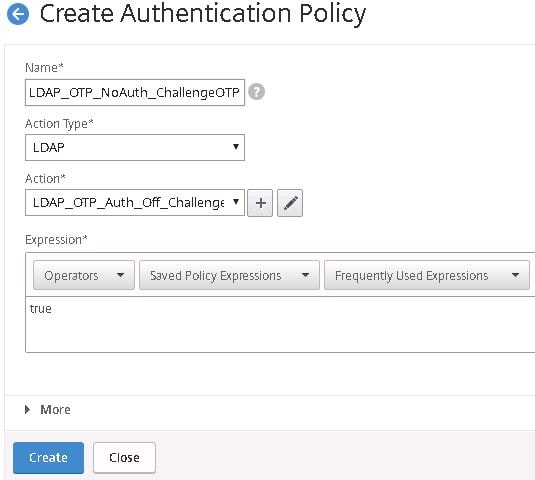
Create a second authentication policy for OTP management using LDAP. Under Action select the LDAP authentication action that has authentication switched off. Under Expression enter HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).EQ(“manageotp”). Using this expression, only users who browse to the OTP management portal will be challenged for this LDAP policy. Click Create.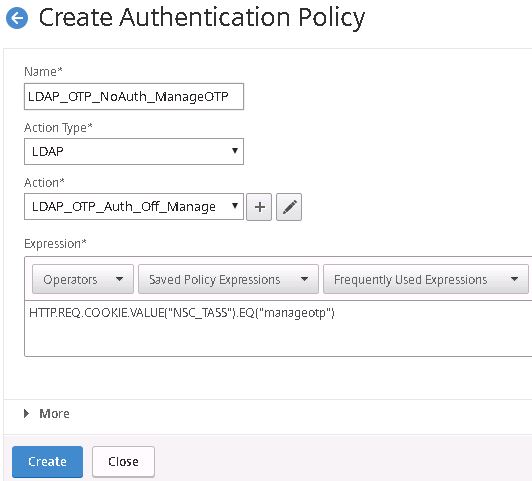
Create a third authentication policy for OTP Challenge using LDAP. Select the same LDAP standard SAN authentication policy that has authentication turned on. Enter an expression of true and click Create.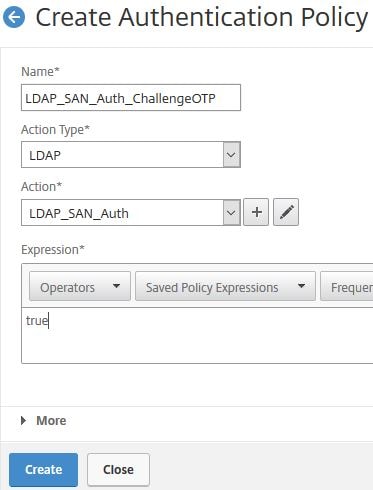
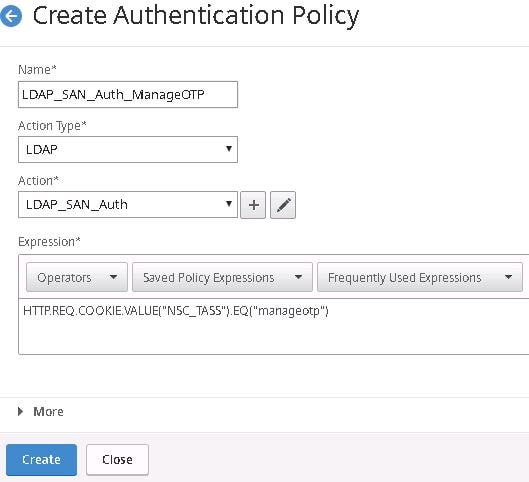
Create a fourth Authentication Policy for OTP Management authentication. Under action select the LDAP SAN policy. Under expression enter HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).EQ(“manageotp”). Click Create.
Create Login Schemas
Next we need to create two Login Schemas. Navigate to Security -> AAA – Application Traffic -> Login Schema -> Profiles -> Add. 
Enter a name for the OTP management portal and under Authentication Schema click the pencil button.
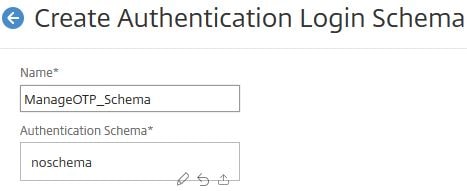
Select the OTP management schema. Click Select. You should create your own schema and place on the NetScaler under directory /nsconfig/loginschema/. I have pasted the Login Schema for OTP management below which you can copy and paste in to your own XML file.
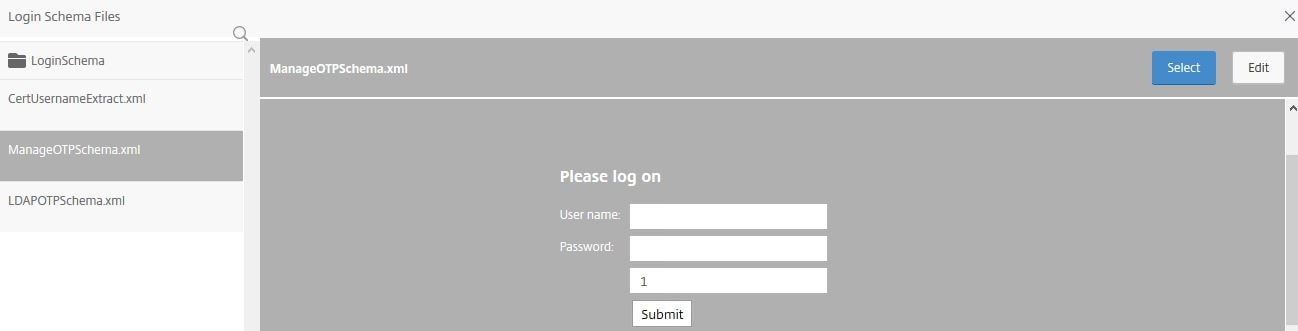
ManageOTPSchema.xml
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <AuthenticateResponse xmlns="http://citrix.com/authentication/response/1"> <Status>success</Status> <Result>more-info</Result> <StateContext></StateContext> <AuthenticationRequirements> <PostBack>/nf/auth/doAuthentication.do</PostBack> <CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack> <CancelButtonText>Cancel</CancelButtonText> <Requirements> <Requirement> <Credential><Type>none</Type></Credential> <Label><Text>Please log on</Text><Type>heading</Type></Label> <Input/> </Requirement> <Requirement> <Credential><ID>login</ID><SaveID>login</SaveID><Type>username</Type></Credential> <Label><Text>User name:</Text><Type>plain</Type></Label> <Input><Text><ReadOnly>false</ReadOnly><InitialValue></InitialValue><Constraint>.+</Constraint></Text></Input> </Requirement> <Requirement> <Credential><ID>passwd</ID><SaveID>passwd</SaveID><Type>password</Type></Credential> <Label><Text>Password:</Text><Type>plain</Type></Label> <Input><Text><Secret>true</Secret><Constraint>.+</Constraint></Text></Input> </Requirement> <Requirement><Credential><ID>otpmanage</ID><Type>none</Type></Credential><Input><Text><Secret>false</Secret><Hidden>true</Hidden><InitialValue>1</InitialValue><Constraint>.+</Constraint></Text></Input></Requirement> <Requirement> <Credential><ID>Logon</ID><Type>none</Type></Credential> <Label><Type>none</Type></Label> <Input><Button>Submit</Button></Input> </Requirement> </Requirements> </AuthenticationRequirements> </AuthenticateResponse>
Click Create.
Now create a second Login Schema, this time for OTP challenges. Enter a name and click the pencil button.
Select your challenge OTP schema under directory /nsconfig/loginschema/. This schema is made up of Username, Password and Passcode boxes for LDAP and OTP factors. Click Select. I have pasted the Login Schema for OTP challenges below which you can copy and paste in to your own XML file.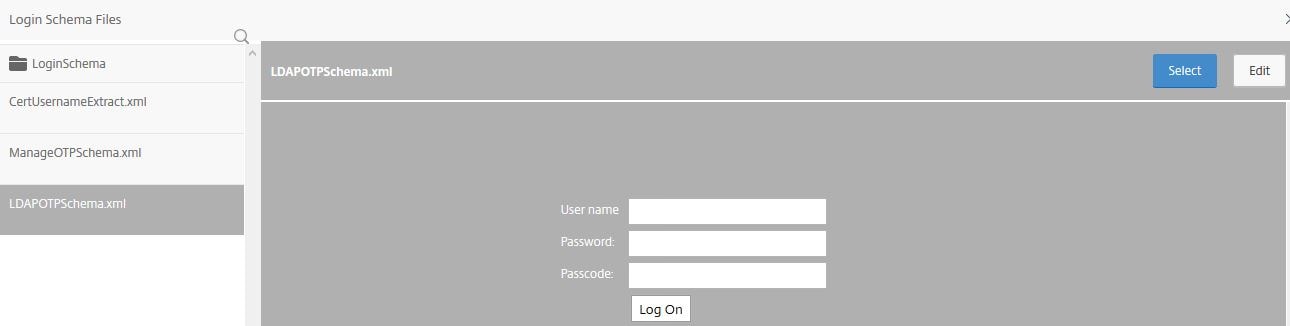
LDAPOTPSchema.xml
<?xml version="1.0" encoding="UTF-8"?> <AuthenticateResponse xmlns="http://citrix.com/authentication/response/1"> <Status>success</Status> <Result>more-info</Result> <StateContext></StateContext> <AuthenticationRequirements> <PostBack>/nf/auth/doAuthentication.do</PostBack> <CancelPostBack>/nf/auth/doLogoff.do</CancelPostBack> <CancelButtonText>Cancel</CancelButtonText> <Requirements> <Requirement><Credential><ID>login</ID><SaveID>ExplicitForms-Username</SaveID><Type>username</Type></Credential><Label><Text>User name</Text><Type>plain</Type></Label><Input><AssistiveText></AssistiveText><Text><Secret>false</Secret><ReadOnly>false</ReadOnly><InitialValue></InitialValue><Constraint>.+</Constraint></Text></Input></Requirement> <Requirement><Credential><ID>passwd</ID><SaveID>ExplicitForms-Password</SaveID><Type>password</Type></Credential><Label><Text>Password:</Text><Type>plain</Type></Label><Input><Text><Secret>true</Secret><ReadOnly>false</ReadOnly><InitialValue></InitialValue><Constraint>.+</Constraint></Text></Input></Requirement> <Requirement> <Credential><ID>passwd1</ID><SaveID>passwd1</SaveID><Type>password</Type></Credential> <Label><Text>Passcode:</Text><Type>plain</Type></Label> <Input><Text><Secret>true</Secret><Constraint>.+</Constraint></Text></Input> </Requirement> <Requirement><Credential><ID>saveCredentials</ID><Type>savecredentials</Type></Credential><Label><Text>Remember my password</Text><Type>plain</Type></Label><Input><CheckBox><InitialValue>false</InitialValue></CheckBox></Input></Requirement> <Requirement><Credential><ID>loginBtn</ID><Type>none</Type></Credential><Label><Type>none</Type></Label><Input><Button>Log On</Button></Input></Requirement> </Requirements> </AuthenticationRequirements> </AuthenticateResponse>
Click More.
Enter 1 in the Password Crential Index box. We want to capture the credentials entered in the first factor for authentication to StoreFront. Click Create.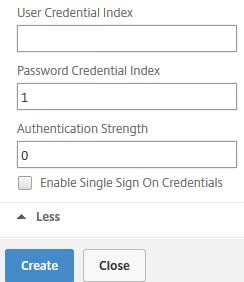
Navigate to the policies tab and click Add. 
Enter a name for the OTP management schema and select the same under Profile. Enter an expression of HTTP.REQ.COOKIE.VALUE(“NSC_TASS).EQ(“manageotp”) which makes sure only users browsing to the OTP management portal receive this Login Schema. Click Create. 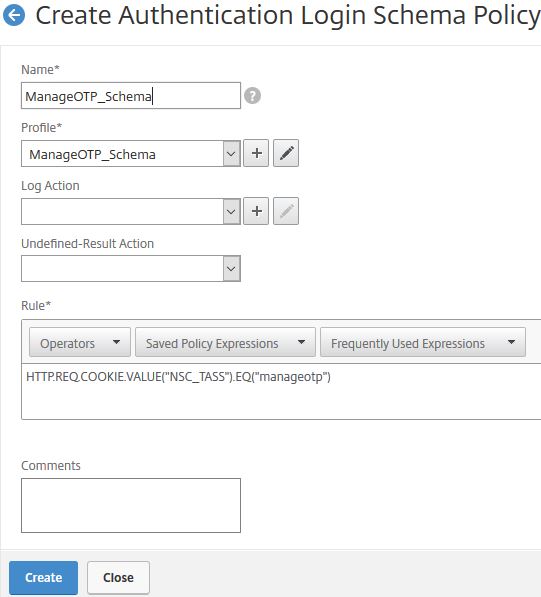
Create another Login Schema for the OTP challenge for users authenticating to NetScaler Gateway. Enter an expression of true. Click Create. 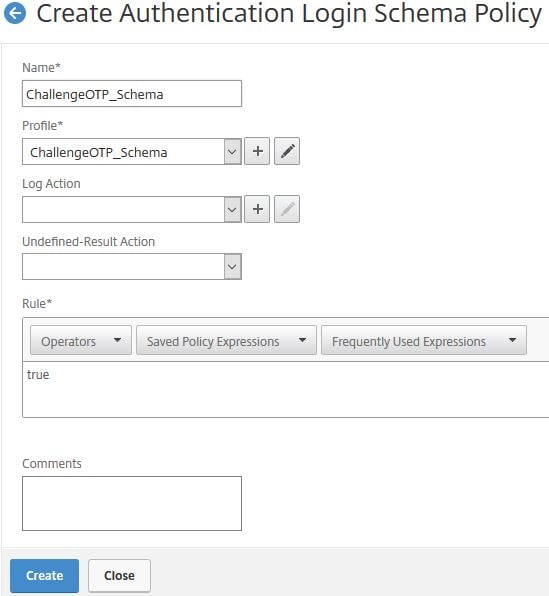
Create Policy Label
To create Policy Labels which contain next factors of authentication, navigate to Security -> AAA – Application Traffic -> Policies -> Authentication -> Advanced Policies -> Policy Labels -> Add. 
Enter a name for the OTP Policy Label. Under Login Schema select LSCHEMA_INT. Click Continue.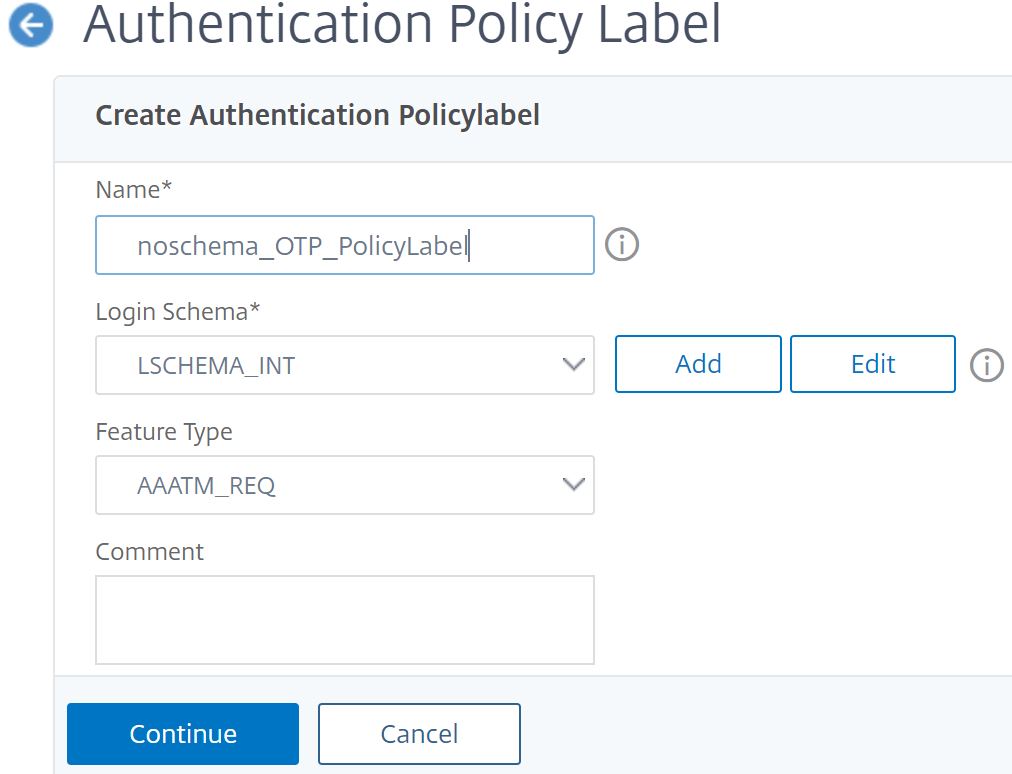
Under Select Policy click Click to select. 
Select the OTP Managment LDAP policy that has authentication is turned off.![]()
Under Goto Expression select END. Click Bind. 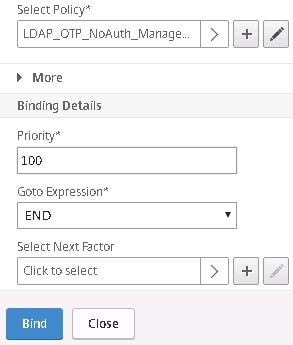
Click Add Binding again. 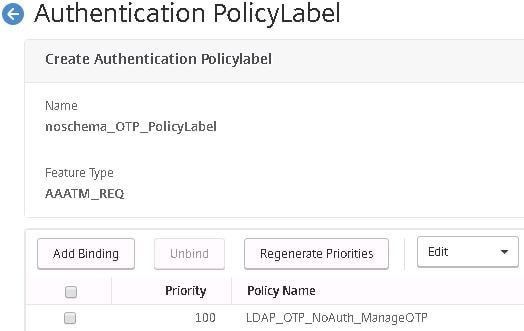
Select the LDAP OTP Challenge policy that has authentication turned off and the Search Filter defined.![]()
Give this policy a higher priority. By default NetScaler will assign a priority of 110. Select END under Goto Expression and click Bind. 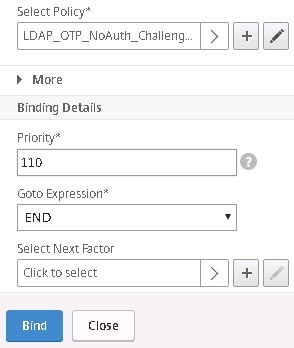
Click Close. 
Create Traffic Policy
Next a Traffic Policy is needed to make sure StoreFront is presented with credentials (username/password) from the correct factor of authentication and not the OTP passcode factor which would obviously result in an error. Navigate to NetScaler Gateway -> Policies -> Traffic Policies -> Traffic Profiles -> Add.
Enter a name and scroll down. 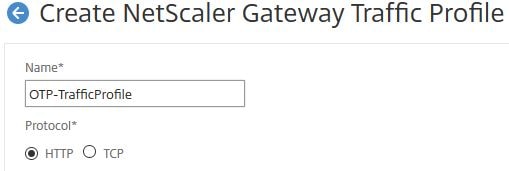
Under SSO Password Expression enter http.REQ.USER.ATTRIBUTE(1) and click Create. 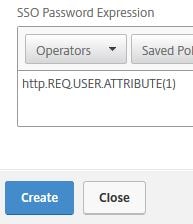
Click the Traffic Policies tab -> Add. 
Enter a name and select the Request Profile you just created. Under Expression enter true. Click Create. 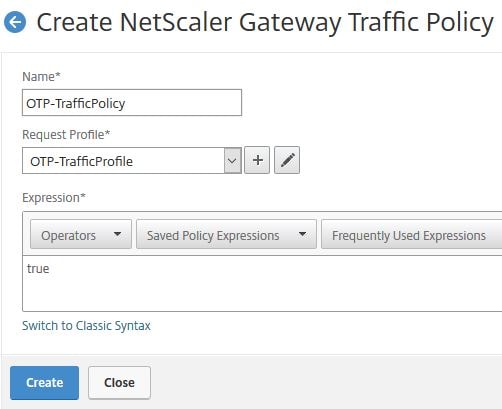
Browse to your NetScaler Gateway virtual server and next to Policies click +. 
Use the drop-downs to select Traffic and Request. Click Continue. 
Click Click to select. 
Select the Traffic Policy you just created. 
Click Bind. 
Bind Login Schemas to AAA vServer
Now we have to bind the Authentication Policies and Login Schemas to the AAA vServer, as well as linking the single Policy Label. Edit your AAA vServer and click No Login Schema. 
Click Click to select. 
Choose the OTP management Login Schema which only evaluates if the users NSC_TASS cookie matches manageotp. ![]()
Click Bind. 
Bind the second Login Schema for LDAP and OTP challenges. That Login Schema should have a higher priority. Anyone not browsing the OTP management URL are presented with an LDAP and OTP schema to authenticate to NetScaler Gateway. Click Close. 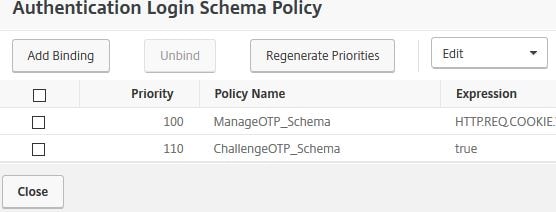
Bind Authentication Policies to AAA vServer
Click No Authentication Policy. 
Click Click to select. 
Select the management OTP LDAP policy which evaluates when users have a NSC_TASS cookie matching manageotp. ![]()
Click Click to select under Select Next Factor. 
Select the noschema OTP Policy Label. ![]()
Click Bind. 
Click Add Binding to begin binding the Authentication Policy for NetScaler Gateway authentication. 
Click Click to select. 
Choose the OTP challenge LDAP policy. This policy have an expression of true for all users accessing the NetScaler Gateway URL.![]()
Under Select Next Factor click Click to select. 
Select the noschema OTP Policy Label. ![]()
Click Bind. 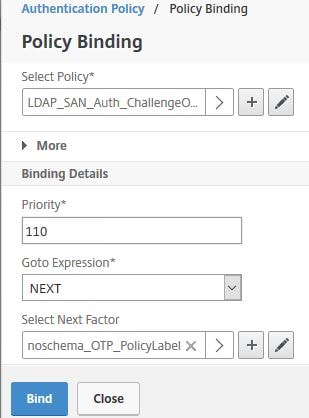
Click Close. 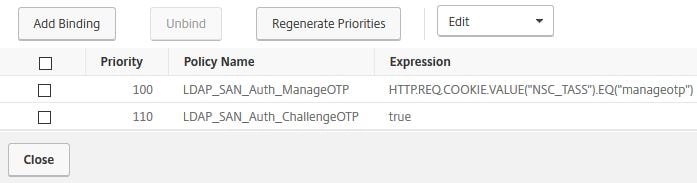
Save the running configuration. The setup is complete.![]()
Enrol Mobile Phones for One-Time Password
Users must firstly enrol their phones to be able to use OTP. The URL they need to use is https://netscalergatewayurl/manageotp. In my case, https://unifiedgateway.jgspiers.com/manageotp. When browsing to this URL, NetScaler sets a cookie against your session which allows the management OTP Login Schema and LDAP authentication policy to evaluate. Enter an LDAP username and password and click Submit.
Note: It would be possible to use a different URL such as https://manageotp.company.com and NetScaler appends the /manageotp directory to the end of the URL. In my case I’m using a single URL pointing to a Content Switch. As mentioned, a second URL could be configured to point to the same Content Switch.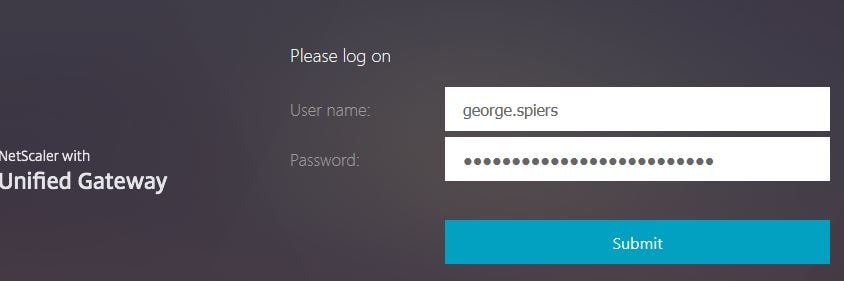
Since this is the first time logging in, no devices will be registered. To register a device click Add Device. 
Enter a name to identity the device your enrolling such as your personal Android or corporate mobile. Click Go.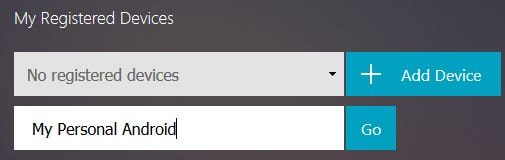
A QR code displays. You’ll need to download Google Authenticator to your phone.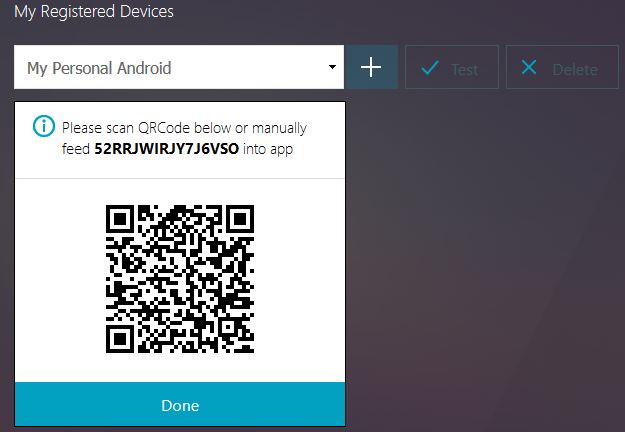
Once downloaded open Google Authenticator and click Scan a barcode. Scan the QR code and then click Done in the OTP management portal. 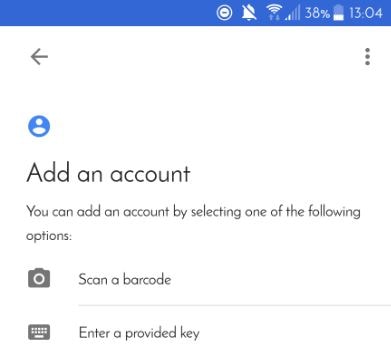
You’ll get the Added successfully! message. To test authentication is working with one-time passwords click Test. 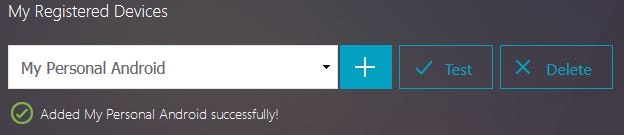
Using your phone, look at the current one-time password. 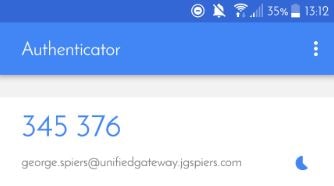
Type this code into the management portal and click Go. You should receive a verification successful message. You can return to the OTP management portal at any time to test authentication, delete devices or add more devices.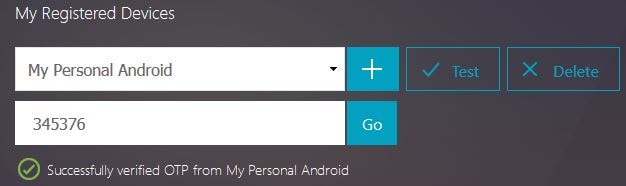
Within Active Directory for users who have enrolled, the userParameters value is updated including the name users specified during enrollment. 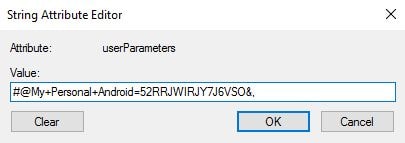
Test One-Time Password Authentication
Now when you want to authenticate with NetScaler Gateway, omit manageotp from your URL, instead entereing https://netscalergatewayurl. Since you aren’t browsing the management OTP URL, no cookie is set and as a result you are presented with the OTP challenge Login Schema. Enter your LDAP credentials and one-time password. Click Log On.
You should successfully authenticate and reach StoreFront. 
Additional Thoughts and Troubleshooting
- As mentioned in the comments. The OTP Management portal is protected by single factor authentication which is unsecure when internet facing. To make this portal more secure you can:
- Protect the portal with additional factors of authentication such as User Certificate.
- Restrict the portal to internal VLANs only using expressions on the Management Login Schema such as HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).EQ(“manageotp”) && CLIENT.IP.SRC.IN_SUBNET(x.x.x.x/24).
- Make use of Server 2016 Active Directory time-based group membership, which makes sure a user only has access to the portal for a short period of time externally and afterwards they have to enrol their phones from the corporate LAN or else request another attempt at enrolling externally using time-based groups.
- A default installation of OTP is unsecure as users who have not enrolled can authenticate to the LDAP+OTP authentication challenge page without entering a one-time password. Because the user has not enrolled, their userParameters attribute in Active Directory will likely be <null>/<not set> and NetScaler will as a result simply accept LDAP credentials and authenticate the user. To get around this, we set a Search Filter on the OTP Challenging LDAP authentication policy. This is all explained in the above guide.
- The NetScaler and client mobile device must have accurate time, otherwise OTP authentication will fail.
- Google Authenticator for example is RFC 6238 TOTP compliant. https://tools.ietf.org/html/rfc6238
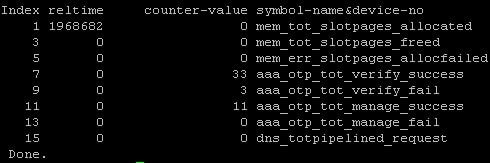
- To view enrolment statistics, you can run command nsconmsg -g otp -d stats. The statistics shown are:
- aaa_otp_tot_verify_success – Total number of successful OTP verifications.
- aaa_otp_tot_verify_fail – Total number of failed OTP verifications.
- aaa_otp_tot_manage_success – Total number of successful enrollments.
- aaa_otp_tot_manage_fail – Total number of failed enrollments.
- When troubleshooting OTP registration or verification, look at the syslog (ns.log) logs. You should also set the log level to DEBUG using command set syslogparams -loglevel DEBUG.
Carl Stalhood
July 24, 2017Do you find it’s too easy to add more OTP devices? You only need single factor auth to access the device registration page, even after a device has already been registered. This means that access to the manageotp page must be restricted.
George Spiers
July 24, 2017Hi Carl. Yeah it is too easy out of the box, as you say it’s protected by just single factor. It would be easy to protect it with more factors if you can using additional Policy Labels, or make the management page internal facing only forcing users to enrol and perform management only from internal locations. Food for thought!
Jochen Hoffmann
August 1, 2017George, first of all: great article, many thanks for that and greetings to Carl btw.
When it comes to the “easy” user device registration, maybe it’s a possibility to create dependency to a specific AD Group Membership, e.g. w/ the according authentication Policy. Yeah, it’s not that smart.
Any possibilty to at some kinda traffic / AppFW policy, so the /manageotp sub URL is available only internally? Anyway, great new feature.
Just some thoughts outta “old europe” … 😉
Cheers, Jochen.
George Spiers
August 1, 2017Thanks. Couple of different options. You can restrict the OTP Management Login Schema by Group Membership as you say, and can also restrict the Login Schema to certain IP ranges. Use default expressions directly on the Management Login Schema policy object to define which conditions should evaluate to true. For example HTTP.REQ.COOKIE.VALUE(“NSC_TASS”).EQ(“manageotp”) && CLIENT.IP.SRC.IN_SUBNET(x.x.x.x/24)
Timo
September 18, 2017Hi!
Regarding this: how about if we plan to use this for external users coming from various sources? These users will have accounts in our AD, but they come from all over. This is the reason we want to apply two-factor authentication. How would we protect the /manageotp in that case? IP-address won’t be an option. Could you explain more about the AD-group option?
George Spiers
September 18, 2017AD Groups basically only allow users who are in a specific AD Group to access the OTP Management Login Schema. So for example, you may be able to use time based Active Directory group membership if you have a forest functional level of Windows Server 2016. If not, you can use standard Group Membership. You could also restrict the OTP Management page to internal IPs. The problem is, when a user has not enrolled for two-factor they have to authenticate to /manageotp to enroll. This is a problem because to authenticate to the OTP Management page they cannot use two-factor (because they have not yet enrolled) so have to use single factor, unless you have another two-factor method. If using single-factor, you have to take extra steps to secure that page.
Shannon
August 2, 2017Nice Article. Maybe a thought is require a Domain Certificate on the PC to be able to enroll a device for OTP. So you’ll have dual factor to enroll a device for OTP. If you are on a nonauthorized device you will not be able to add a mobile device for OTP.
George Spiers
August 2, 2017Thanks and yes there are many different ways to go about it 🙂
JD Mac
July 25, 2017Is there a private release of the 51.24 firmware needed to enable this feature? I’m running that code version and my NetScaler does not show the “OTP Secret” field on the “Create Authentication LDAP Server” screen.
George Spiers
July 25, 2017No private builds. The public release is the one you need. 12.0.51.24.
Are you running this build in production or a lab?
JD Mac
July 26, 2017It’s a Plat VPX running in a lab. The VPX promises it’s on 12.0.51.24.nc 🙂 That field is simply missing from the config screen.
George Spiers
July 26, 2017Can you run the following command as a test? “add authentication ldapAction test -serverName test -ldapBase test -ldapBindDn test -ldapBindDnPassword 123 -authentication DISABLED -OTPSecret 123” If that works, OTP is there but for some reason not showing in GUI. I’d suggest building another VPX. I’ve not seen it personally before and have upgraded a few appliances.
JD Mac
July 26, 2017Well, look at that. The parameter is there on the CLI. I’ll do my test config from CLI and redeploy the thing when I have a few minutes. Thanks!
Carl Stalhood
July 26, 2017What Portal Theme do you have on your Gateway vServer?
JD Mac
July 26, 2017The Gateway is set to RfWebUI.
Carl Stalhood
July 26, 2017Hmm, I’m getting “please select one of the following” when I assign RfWebUI to Gateway. If I select X1 theme and leave RfWebUI on AAA, then everything works.
Carl Stalhood
July 26, 2017I figured out my RFWebUI problem. It’s caused by enabling HSTS in the Default Front End SSL Profile. This setting also broke my manageotp page.
George Spiers
July 27, 2017Thanks Carl, I replicated what you are seeing also here in my lab. Looks like the old way of inserting the STS header via Rewrite works..
George Spiers
September 28, 2017This is now acknowledged by Citrix as an issue. https://support.citrix.com/article/CTX228504
Jacob Dixon
July 27, 2017I am testing this out and running into a couple of issues. When I click submit when logging in, the submit button turns to a refresh and just hangs. Chrome dev tools shows:
Uncaught ReferenceError: _localize is not defined
at Object.getLabelTypeMarkup (https://access.compsyscloud.com/logon/LogonPoint/plugins/ns-gateway/ns-nfactor.js:91:41)
at Object.addStandaloneLabel (and more……)
The other issue is when I refresh the page I am presented with the “My Registered Devices” page. I think there should be a “Done” button somewhere to let the user get back to the login or get to storefront. Doesn’t seem very straight forward unless I have something configured incorrectly.
Jacob Dixon
July 27, 2017I figured out what it was. I had the ChallengeOTP_Schema profile bound to the wrong authentication schema (was set to ManageOTPSchema.xml which is wrong).
Let me ask you this though, is it possible to configure this to present a new page for the OTP only if the user belongs to a specific security group?
Like most OTP there are normal steps:
* User Logs In
* If user is supposed to have OTP and hasn’t setup OTP then present the Add Devices page
* If user is supposed to have OTP and is setup, then present a new page to get the OTP
* User is presented storefront page after correct OTP is entered
George Spiers
July 27, 2017Absolutely. So for example you could have one group in AD where members are those users who have registered with OTP. All other non-members are simply not OTP registered. When users authenticate with NetScaler, group extraction is performed and if users are members of the group they get the Challenge OTP schema. If users are not, they receive the Register OTP schema. To determine what Schema to present users with, expressions on NetScaler would be used such as “HTTP.REQ.USER.IS_MEMBER_OF(“OTPGroup”)”. You’d have to keep the OTP Group up to date though with users who have enrolled. That wouldn’t be the NetScaler’s job.
Jacob
April 26, 2018I haven’t tried this yet but I’m going to now. It is too bad this doesn’t work with Citrix Receiver still.
Timco Hazelaar
July 28, 2017Aloha George,
Great article, but I have one question.
I followed your article, all is working fine, except for the SSO part to StoreFront. I think its mixing up “username” and “password” for SSO. In the eventlog on my StoreFront it states that user is trying to logon. And “MyPassword” is actually my password for my LAB infra… I double checked the “password credential index” field, which is 1..
Regards,
Timco
George Spiers
July 28, 2017Did you create the Traffic Policy and bind it to your NetScaler Gateway vServer? Doing that, and setting an index of 1 on the Challenge OTP schema is required.
Daniel Weppeler
July 28, 2017Which rights have your service user “svc_ns” ?
I’ve get some error messages (aaad.debug log):
+++++++++++++
Fri Jul 28 14:07:10 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/ldap_common.c[260]: ns_show_ldap_err_string 0-305: LDAP error string: <>
Fri Jul 28 14:07:10 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/ldap_common.c[446]: ns_ldap_check_result 0-305: LDAP action failed (error 50): Insufficient access
+++++++++++++
George Spiers
July 28, 2017You need at minimum permission to be able to read and write to the userParameters attribute. You can use delegation in AD to grant the service account with those permissions.
Pingback: EUC Weekly Digest – July 29, 2017 – Carl Stalhood
lowdez
July 30, 2017Hey, great article ! thank you !
I’ve followed your documentation to the letter and having issues when registering the mobile device –
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/ldap_drv.c[554]: receive_ldap_user_search_event 0-261: User search succeeded, attempting user authentication(Bind) for
Sun Jul 30 12:35:55 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/ldap_drv.c[558]: receive_ldap_user_search_event 0-261: noauth, preparing to update otp in attribute for , devicelen 7, devicename mobile
Sun Jul 30 12:35:55 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/ldap_common.c[1466]: ns_ldap_register_otp 0-261: Attempt to manage otp when otp attribute is not defined!, sending reject
Sun Jul 30 12:35:55 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/naaad.c[3322]: send_reject_with_code 0-261: Not trying cascade again
Sun Jul 30 12:35:55 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/naaad.c[3324]: send_reject_with_code 0-261: sending reject to kernel for : testacc
Sun Jul 30 12:35:55 2017
/home/build/rs_120_51_22_RTM/usr.src/netscaler/aaad/naaad.c[3327]: send_reject_with_code 0-261: Rejecting with error code NULL
George Spiers
July 30, 2017Sounds like you don’t have the OTP Secret field completed in your LDAP profile? Under the field “OTP Secret” you should enter “userParameters” without the quotation marks.
Lowdez
July 30, 2017Yes ! that’s the one, must’ve missed it.
Thank you !
Igor
August 2, 2017Excellent examples.
I have been able to repeat and consolidate your examples login
1. Certificates
2. OTP.
The question is how to solve the problem
The same user receives a different profile at logon 1 and 2
It’s probably because
If you log on to a certificate, use the userPrincipalName =(username/domen) field
With OTP-sAMAccountName =(username)
Thank you!
George Spiers
August 2, 2017On your AAA vServer you could have a cert authentication policy bound with priority 100 with nextfactor set to PolicyLabel which has a UPN LDAP Policy attached. The AAA vServer can have a second authentication policy attached (higher priority e.g. 110) for when certificate authentication fails. This policy uses the OTP/SamAccountName LDAP policies and OTP challenge PolicyLabel..
Igor
August 5, 2017Thank you!
Pingback: NetScaler Gateway 12 Native One Time Passwords (OTP) – Carl Stalhood
Steve Ludlow
August 4, 2017I have a query. Pretty sure I have this configured as documented. With the LDAP server that has authentication disabled and userParamters>=#@ in the Search filter no users can login once registered, just get a “Try again or contact your help desk” error.
If I remove the userParamters>=#@ from the search filter then I can log in with OTP. But obviously users that are not enrolled can also login without entering an OTP.
Any clues as to what is going on here?
George Spiers
August 4, 2017If you look in AD for an affected (OTP registered) user, under the Attribute Editor tab what value is set for userParameters?
I assume that users can log on to the Management OTP all the time, regardless if userParameters>=#@ is set? You should have two LDAP policies with authentication turned off. One for Challenging front-end authentication with userParameters>=#@ set and a second strictly for the OTP Management portal without userParameters>=#@.
Steve Ludlow
August 4, 2017So in userparameters for an AD account I have #@OP3T=GZHGSGC2NXQ2GIOU&, for example.
Yes, can log into the management OTP all the time without issue.
And yes, LDAP Polices setup exactly as described.
George Spiers
August 4, 2017Interesting, run a cat aaad.debug from CLI for a single login that fails with this error. Feel free to post the output here or to my email george@jgspiers.com
Sebastian K.
November 28, 2017what is the solution? ive got a near error…
when i add the OTP Secret to the challenging policy i cant Login, neather to the challenging, as in the Management Portal.
when i clear the OTP Secret field in the challenging policy i can Login in the Management, and also in the Challenging Portal, BUT it didnt check the OTP Secret…
Citrix is working sind 18 days to find somebody who supporting this… >.<
Could you help me?
George Spiers
November 29, 2017Use an LDAP bind account on your Challenge/ManageOTP LDAP profiles that has both read and write access to the userParameters attribute in Active Directory.
Sebastian
November 29, 2017No Reply button at my comment, so here the answer:
Sebastian
November 29, 2017No Reply button at my comment, so here the answer:
i’ve used the Domain Administrator, and also everybody got total write Access for User Objects.
Other Idea?
George Spiers
November 30, 2017Run “cat aaad.debug” from NetScaler CLI and see if you can see anything in the logs. https://jgspiers.com/netscaler-authentication-failures-aaad-debug/https://jgspiers.com/netscaler-authentication-failures-aaad-debug/ also make sure your Login Schemas are configured correctly using the XML code I provided.
Sebastian K
November 30, 2017copied your XML files as a other XML files, and bind it again.
Doesnt work…When i add to the manageotp LDAP Server with Domain User assigned(but without authentication), and granded everybody Read and Write Access to the User Attribute userParameters, i cant even log in in the Manageotp.
Hier are the aaad.debug… i cant find any Errors with this…do you see something?(Variables replaced and hidden in the outbut through [My…]):
root@S35-NS01# cat aaad.debug
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[845]: process_kernel_socket 0-701: partition id is 0
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[1082]: process_kernel_socket 0-701: call to authenticate
user :[MySamAccountName], vsid :16261, req_flags 2
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[3820]: start_cascade_auth 0-701: starting cascade authentication
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[107]: start_ldap_auth 0-701: Starting LDAP auth
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[131]: start_ldap_auth 0-701: attempting to do ldap auth for [MySamAccountName] @ [MyLDAPServer]
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[133]: start_ldap_auth 0-701: LDAP referrals are OFF
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[134]: start_ldap_auth 0-701: LDAP referral nesting depth 0
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[721]: continue_ldap_init 0-701: Connecting to: [MyLDAPServer]:389
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[727]: continue_ldap_init 0-701: User [MySamAccountName] Connecting to: [MyLDAPServer]:389
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4119]: register_timer 0-701: setting timer 1172
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4196]: unregister_timer 0-701: releasing timer 1172
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[801]: ns_ldap_set_up_socket 0-701: Server certificate hostname = NULL
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[846]: ns_ldap_set_up_socket 0-701: Set cert verify level 0
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[849]: ns_ldap_set_up_socket 0-701: Getting cipher suite global value
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[852]: ns_ldap_set_up_socket 0-701: Checking non-zero cipher suite
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[862]: ns_ldap_set_up_socket 0-701: NULL cipher suite. Using default.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[868]: ns_ldap_set_up_socket 0-701: Freeing cipher suite value
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[875]: ns_ldap_set_up_socket 0-701: Done with cipher suite
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[944]: ns_ldap_set_up_socket 0-701: Sectype: 1
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[949]: ns_ldap_set_up_socket 0-701: Successfully established connection to NULL
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4119]: register_timer 0-701: setting timer 1173
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[187]: receive_ldap_bind_event 0-701: receive ldap bind event
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 0-701: checking LDAP result. Expecting 97 (LDAP_RES_BIND)
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[436]: ns_ldap_check_result 0-701: ldap_result found expected result LDAP_RES_BIND
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[199]: receive_ldap_bind_event 0-701: Bind OK
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4196]: unregister_timer 0-701: releasing timer 1173
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[268]: receive_ldap_bind_event 0-701: Original slen: 5
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[292]: receive_ldap_bind_event 0-701: User name: dirty = sanitized =
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[294]: receive_ldap_bind_event 0-701: Admin bind successful, attempting user search event for [MySamAccountName]
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-701: OTP Secret Attribute name: , length 6
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[1078]: ns_ldap_search 0-701: Searching for <=#@))>> from base <>
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4119]: register_timer 0-701: setting timer 1174
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[1102]: ns_ldap_search 0-701: Sent user search query.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[345]: receive_ldap_user_search_event 0-701: Received LDAP user search event.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 0-701: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[402]: ns_ldap_check_result 0-701: Got result 0. Non-event, continuing
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[345]: receive_ldap_user_search_event 0-701: Received LDAP user search event.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 0-701: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[402]: ns_ldap_check_result 0-701: Got result 0. Non-event, continuing
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[345]: receive_ldap_user_search_event 0-701: Received LDAP user search event.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 0-701: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[402]: ns_ldap_check_result 0-701: Got result 0. Non-event, continuing
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[345]: receive_ldap_user_search_event 0-701: Received LDAP user search event.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 0-701: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[402]: ns_ldap_check_result 0-701: Got result 0. Non-event, continuing
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[345]: receive_ldap_user_search_event 0-701: Received LDAP user search event.
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 0-701: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[436]: ns_ldap_check_result 0-701: ldap_result found expected result LDAP_RES_SEARCH_RESULT
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[357]: receive_ldap_user_search_event 0-701: received LDAP_OK
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4196]: unregister_timer 0-701: releasing timer 1174
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[387]: receive_ldap_user_search_event 0-701: Binding user… 1 entries
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[388]: receive_ldap_user_search_event 0-701: Admin authentication(Bind) succeeded, now attempting to search the user [MySamAccountName]
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[414]: receive_ldap_user_search_event 0-701: User DN= <>
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-701: OTP Secret Attribute name: , length 6
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[584]: extract_ldap_attribute 0-701: retrieved ntotp value #@iPhoneArbeit=[TokenID_1],iPhoneArbeit2=[TokenID_2], for [MySamAccountName], length is 65
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-701: OTP Secret Attribute name: , length 6
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[498]: receive_ldap_user_search_event 0-701: extracted attribute, name: ntotp, value: #@iPhoneArbeit=[TokenID_1],iPhoneArbeit2=[TokenID_1],
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-701: OTP Secret Attribute name: , length 6
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[515]: receive_ldap_user_search_event 0-701: For user [MySamAccountName], group stringLength 273
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[524]: receive_ldap_user_search_event 0-701: built group string for [MySamAccountName] of:G_CAGVPN
…
…
Remotedesktopbenutzer
Domänen-Admins
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[533]: receive_ldap_user_search_event 0-701: Authentication is disabled for user [MySamAccountName], finishing ldap authentication
Thu Nov 30 17:32:52 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[2969]: send_accept 0-701: sending accept to kernel for : [MySamAccountName]
Sebastian K
November 30, 2017also i didnt use userParameters, i use ntotp, which i created in the Domain Schema.
George Spiers
November 30, 2017So under OTP Secret you are using “ntotp”? If you change that temporarily to userParameters does it work. Are you using a search filter on your LDAP profiles? If so, remove it temporarily and see if it works.
Sebastian K
November 30, 2017Neather userParameters nor searxh Filter. We didnt use a search Parameter
George Spiers
November 30, 2017So try using userParameters to see if you experience the same issue.
Sebastian K
December 4, 2017Sorry for my Bad english.
I tried userParameters, bei This also didnt work
George Spiers
December 4, 2017OK so if you follow this article closely, it should work. I suggest you try this on a test NetScaler appliance running the latest version, and you then may be able to compare it to your own production configuration to see what is wrong.
Igor
August 9, 2017I’m checking the user’s identity to the group. Detected if the OTP device is not registered, you can log on to the system without an access code. I had to make a complicated filter.
&(userParameters>=#@)(memberOf:1.2.840.113556.1.4.1941:= CN=NetScalerExtUser,CN=Users,DC=v…..,DC=s…,DC=…)
Ciprian
August 4, 2017What if you have GSLB serving one single URL around the globe ? Will the same OTP work on different Netscaler pairs part of the GSLB .. not sure how the OTP is generated therefore I’m just asking if this is possible ..
Thank you
George Spiers
August 4, 2017Yes it will work just fine. So long as the NetScaler appliances all probe the same Active Directory domain for authentication!
man
May 6, 2019Hi George,
I am facing issue when try to set AD user account lockout duration changed to 30 mins from 1 min.
when changed the value from 1 min to 30 mins users were unable to login on netscaler and getting incorrect user id and password. this setting only does not work for citrix ldap account on AD. This account is a member of group account lock out duration is set for 1 min. Any idea what might have caused this issue ?
George Spiers
May 9, 2019When everything works, what is the lockout duration for both standard user accounts and the LDAP bind account? Likewise, when things do not work, what is the lockout duration for both standard user accounts and the LDAP bind account?
Stan
August 11, 2017So I can register my device fine. I can see that the attribute/property is updated correctly in AD. However, when I test, I don’t go any further than ‘Test failed for my phone’.
Thoughts?
George Spiers
August 11, 2017You are testing and getting this error using the Manage OTP portal or when trying to log on to NetScaler Gateway? Run an AAAD Debug using CLI to see if you can pick up any pointers as to why it is failing.
Pingback: Detailed Change Log – Carl Stalhood
Srini
September 12, 2017I followed your article and got OTP working for RfWeb, but services site with native Receiver client is not working. When adding an account, Receiver challenges for OTP but the authentication fails. I have not checked AAAD logs yet, wanted to check if you have tested services site using Receiver client.
Srini
September 12, 2017I just read Carl’s blog and found that OTP uses nFactor & that doesn’t support Receiver clients
George Spiers
September 12, 2017Correct. nFactor is not yet supported for native Receiver clients.
Jeff Sani
September 17, 2017Hey George,
Thanks for all these great articles. One typo to correct in your post:
Enter a name for the OTP LDAP Management policy. Under Action select the LDAP SAN action. Enter an expression of HTTP.REQ.COOKIE.VALUE(“NSC_TASS).EQ(“manageotp”) and click Create.
The reference image actually has a different name displayed. Minor thing but thought you might want to know. I agree with your comments about the documentation and I already voiced concern about it and am working with PM to improve it. I can tell you that much of the other feedback about the missing controls is being addressed. This is V1 of this great feature and so far the feedback has been overwhelming so I think it was a hit. Thank you again for all your contributions.
Regards,
Jeff
George Spiers
September 18, 2017Thanks for pointing that out Jeff. I corrected the screenshot. Regarding documentation I can’t remember making any comments on that, but agree it is a great feature which my customers are already embracing!
Pingback: Citrix Federated Authentication Service: Azure AD as Identity Provider – dready's Blog
Bourke
November 10, 2017Hi:
is there a way to create a dedicated internal vserver just to serve device registration, then create 2nd vserver for the Internet without the device registration capability at all ? or at least some how cripple the device registration function on the 2nd vip , (something more than a http.req.cookie.value(\”NSC_TASS\”).eq(\”manageotp\”) && client.IP.SRC.IN_SUBNET(192.168.100.0/24) ” rules
George Spiers
November 10, 2017Yes you could do. You would just bind the Manage OTP Login Schema and related policies to an internal AAA vServer.
Mark Brilman
November 10, 2017Hi George,
I implemented it following your guide which is great. All works well and clients get presented with working 2-factor authentication like they should.
However I noticed accessing the /manageotp page does present a 2-factor schema, I can just authenticate with 1-factor just fine (only LDAP).
Although I see OTP fail in aaad.debug NetScaler doesn’t seem to care. Do you have a clue why?
I used extensionAttribute1 cause there’s something Citrix related in UserParameters already.
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[357]: receive_ldap_user_search_event 0-643: received LDAP_OK
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4196]: unregister_timer 0-643: releasing timer 471
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[387]: receive_ldap_user_search_event 0-643: Binding user… 1 entries
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[388]: receive_ldap_user_search_event 0-643: Admin authentication(Bind) succeeded, now attempting to search the user MyUserName
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[414]: receive_ldap_user_search_event 0-643: User DN= <>
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-643: OTP Secret Attribute name: , length 20
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[520]: extract_ldap_attribute 0-643: While retrieving ldap attributes extensionAttribute1 attribute not found for MyuserName
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-643: OTP Secret Attribute name: , length 20
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[495]: receive_ldap_user_search_event 0-643: Failed to extract attribute, name: extensionAttribute1,
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 0-643: OTP Secret Attribute name: , length 20
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[515]: receive_ldap_user_search_event 0-643: For user MyUserName, group stringLength 99
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[524]: receive_ldap_user_search_event 0-643: built group string for MyUserName of:Couple
Of
Groups
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[533]: receive_ldap_user_search_event 0-643: Authentication is disabled for user MyUserName, finishing ldap authentication
Fri Nov 10 16:41:59 2017
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[2969]: send_accept 0-643: sending accept to kernel for : MyUserName
Relevant Config
add authentication ldapAction AS_LDAPS_OTP_NOAUTH -serverIP 192.168.xxx -serverPort 636 -ldapBase “dc=xxx” -ldapBindDn SVC-xxx@xxx.local -ldapBindDnPassword xxx -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName samAccountName -groupAttrName memberOf -subAttributeName CN -secType SSL -authentication DISABLED -passwdChange ENABLED -OTPSecret extensionAttribute1
add authentication ldapAction AS_LDAPS_OTP_NOAUTH_VERIFY -serverIP 192.168.xxx -serverPort 636 -ldapBase “dc=xxx” -ldapBindDn SVC-xxx@xxx.local -ldapBindDnPassword xxx -encrypted -encryptmethod ENCMTHD_3 -ldapLoginName samAccountName -searchFilter “extensionAttribute1>=#@” -groupAttrName memberOf -subAttributeName CN -secType SSL -authentication DISABLED -passwdChange ENABLED -OTPSecret extensionAttribute1
George Spiers
November 10, 2017The guide doesn’t protect /manageOTP with 2-factor. By default /manageOTP is only protected by LDAP, unless you perform additional modifications not explained in this guide.
Normally users who have not enrolled have not yet got 2-factor, so can only use single factor to /manageOTP and then we secure the /manageOTP page for internal access only.
David Webb
December 4, 2017Excellent Article works well with web client. Any new on when Native OTP will be supported by receiver? Or a workaround to allow OTP to happen for web client and LDAP for receiver until then?
George Spiers
December 28, 2017I haven’t any information as to when we can get OTP working via native Receiver yet. If you want to lock the OTP policy down to web clients, then use an expression such as “HTTP.REQ.HEADER(“User-Agent”).CONTAINS(“CitrixReceiver”).NOT” against the OTP policy.
Zack
December 4, 2017We would love to see the native OTP work with receiver as well. It is a show stopper for us until then.
Jeff
December 4, 2017See: https://support.citrix.com/article/CTX223386
You can also use policy expressions at your loginschema and Authentication VServer for presenting a supported native client flow. i.e.:
HTTP.REQ.HEADER(“User-Agent”).CONTAINS_ANY(“ns_vpn_client_useragents”)
Also, Latest version of Receiver supposedly has added support for Authv3 forms. I have not tried this out myself yet. Some of the embedded Auth extensions like Captcha or Swivel may not work, but other step-through flows may.
David Webb
December 4, 2017I actually gave that a shot working with citrix support with no luck. The tech created a seperate policy called “receiveronly” and tried REQ.HTTP.HEADER User-Agent CONTAINS CitrixReceiver, with no luck.
idan david
December 21, 2017Hi
after i finish to configure it i have 2 problem
1.when i add new device and click GO to get QR code nothing heppand
2. when i make login to the site i get old netscaler GUI
George Spiers
December 21, 2017Make sure the portal theme is set to “RfWebUI”
idan
December 25, 2017thanks its work
one more question after i bind the traffic policy when i`m connecting to full vpn i cant do anything , only ping and http website work , how i can solved this
idan
January 1, 2018the traffic policy the set to true block non http connection like tcp
how can i allow non http traffic and http traffic with this policy
George Spiers
January 2, 2018You can change the expression so that it only matches authentication traffic. Try: HTTP.REQ.URL.CONTAINS(“/nf/auth”)
idan
January 2, 2018i solved it by change the expression to “http.req.method.eq(post) ||http.req.method.eq(get) && false”
thanks anyway
Srini
January 7, 2018Hi George,
I followed your article and setup a POC, everything worked as expected. Now I need to production deployment in a phased manner, so I have created 2 groups ExternalAccess-LDAP & ExternalAccess-OTP.
1. NS GW access is not restricted to a group today
2. I want to present just the username screen, get the user name and present with next factors based on membership – either password only or password and OTP. I need to change the default login schema to username field only.
3. Once all the users are onboard with OTP, I will leave the LDAP group empty so that I can use it as back door entry if needed in future. User lost the mobile, etc.
4. Native Receiver authentication policy should be user name and password, I will restrict it to a separate group as Native Receiver doesn’t support OTP.
I followed this article to create diff authentication policies based on group membership, I am not able to present different login schemas based on the factor.
https://support.citrix.com/article/CTX222713
Can you suggest how should i go about it?
Thanks.
George Spiers
January 8, 2018You could use a NO_AUTHN Authentication Policy (one for LDAP, one for OTP) and these Authentication Policies have expressions that look for group membership. Each policy then sends you to a Policy Label which only has either the LDAP schema (and LDAP policy) or sends you to a OTP Policy Label which presents users with the OTP Login Schema and LDAP/OTP policies. Have a look here as I use NO_AUTHN policies -> https://jgspiers.com/nfactor-authentication-with-netscaler-gateway/
Srini
January 9, 2018I followed your blog and configured next factor based on group membership, but when i present username only login schema after entering username i get “System error” and that doesn’t go any further. This repeats with any user account.
George Spiers
January 9, 2018You can bind the Username only Login Schema directly to the AAA vServer so all users in the first instance are presented with this Login Schema. Then have an Authentication Policy for Group Extraction bound to the AAA vServer with next factor as a Policy Label which has noschema bound to it. This Policy Label with noschema has two NO_AUTHN policies bound to it. One for LDAP only and one for LDAP+OTP. The LDAP only NO_AUTHN (which has an expression looking for AD LDAP group) is configured with next factor to a LDAP only Policy Label which has a LDAP only Login Schema bound and a LDAP policy bound. The LDAP+OTP NO_AUTHN policy (which has an expression looking for AD+OTP LDAP group) is configured with a next factor to a LDAP+OTP Policy Label which has a LDAP+OTP Login Schema bound and an LDAP+OTP auth policy bound.
Srini
January 9, 2018Group extraction works after fixing LDAP-GroupExtraction action. However, i get “Cannot Complete Request” upon logging in from StoreFront server. I tested StoreFront directly and it works.
Srini
January 9, 2018SSO failed. Citrix Authentication service – Error ID 7 om StoreFront server
CitrixAGBasic single sign-on failed because the credentials failed verification with reason: Failed.
The credentials supplied were;
user: Test User 2
domain: XXXXX
George Spiers
January 9, 2018Does this happen when you peform single LDAP authentication to NetScaler or LDAP+OTP/both? Is that username wrong or correct? Is the domain name correct? Have you confirmed that the LDAP policy (not the one used for username extract) has “Authentication” checked within the LDAP profile and it is receving hits when it should i.e. it is evaluating after you perform the username extraction?
Srini
January 9, 2018George – I was able to resolve the issue with SSO, i had to create a new Traffic Policy with User & Password credential index. The one i used earlier for OTP POC had only Password index.
Thanks for all your help.
George Spiers
January 9, 2018No problem. I suspected that it was an issue with Traffic Policies!
Tobias
January 9, 2018Hi Carl
Thank you for this very useful documentation.
I still have an issue. When trying to add an device I can type in the name but I when click on OK nothing happens.
Do you have any idea why?
Regards Tobias
George Spiers
January 9, 2018Sounds like your NetScaler “Administrator Bind DN” account does not have enough permissions. It should be able to both read and write to the userParameters Active Directory attribute for each enrolling user.
Pingback: NetScaler native OTP does not work for users with many group memberships | vcloudnine.de
Anonymous
February 1, 2018Thank you for posting this blog. Very helpful.
Is it possible to edit the Key Uri Format (issuer field) so that my users will have a nice label to know this is the correct code for our NetScaler?
https://github.com/google/google-authenticator/wiki/Key-Uri-Format
Cheers Brendon
George Spiers
February 1, 2018Sorry not sure I understand your requirement Brendon.
Brendon Higgins
February 8, 2018When I open my Google Authenticator app on my mobile phone, I see 6 different sets of numbers for different services I use. The new NetScaler one shows A_NAme@MyDomain.com in small font letters under the large font OTP number. Other services have used the ‘issuer field’ to create a medium font & bold label over the OTP number. I would like to set this as “CompanyName Remote Access”.
Do you know if this is possible? Manually entering the key enables users to set the Account name to be anything they like but I don’t want to recommend this option.
Sebastian
February 8, 2018interesting idea…hooking in to follow the answers;)
George Spiers
February 12, 2018Please open a support case and submit an Enhancement Request.
hung
February 12, 2018Hi
I am testing this now and just wonder if Netscaler Native OTP can challenge user using sms/hardware token?
In this article I believe we are using google authenticator
George Spiers
February 12, 2018Anything that is RFC 6238 compliant is what NetScaler OTP supports.
Ken Zygmunt
March 27, 2020George
have you come across anything/anyone who’s gotten SMS or hardware tokens to work with the NetScaler OTP?
Thanks
George Spiers
May 19, 2020No and do not believe hardware tokens can be used yet due to a limitation.
Anton
February 14, 2018Hi George,
Thank you for the nice article. Great work!
I had one issue which you mentioned in troubleshooting section from your article. I was not able to pass test when I enrolled my phone. The issue was different time between my phone and my netscalers.
I am wondering in next coming release of NetScaler is it support as well local Citrix Receiver to authenticate with OTP also. Do you know?
Thank you!
George Spiers
February 14, 2018No plans yet as to when Receiver will support nFactor.
Srini
February 21, 2018Hi George,
I followed your article and got OTP setup configured in my environment. OTP is not working for one user out of 6 users tested. Find below the aaad.debug log. Note: I have removed base DN and user DN from the log.
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 1-108989: OTP Secret Attribute name: , length 15
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[1078]: ns_ldap_search 1-108989: Searching for <=#@))>> from base <>
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4119]: register_timer 1-108989: setting timer 567794
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[1102]: ns_ldap_search 1-108989: Sent user search query.
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[345]: receive_ldap_user_search_event 1-108989: Received LDAP user search event.
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[398]: ns_ldap_check_result 1-108989: checking LDAP result. Expecting 101 (LDAP_RES_SEARCH_RESULT)
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[436]: ns_ldap_check_result 1-108989: ldap_result found expected result LDAP_RES_SEARCH_RESULT
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[357]: receive_ldap_user_search_event 1-108989: received LDAP_OK
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/naaad.c[4196]: unregister_timer 1-108989: releasing timer 567794
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[387]: receive_ldap_user_search_event 1-108989: Binding user… 1 entries
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[388]: receive_ldap_user_search_event 1-108989: Admin authentication(Bind) succeeded, now attempting to search the user tuser2
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[414]: receive_ldap_user_search_event 1-108989: User DN= <>
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 1-108989: OTP Secret Attribute name: , length 15
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_common.c[584]: extract_ldap_attribute 1-108989: retrieved userParameters value #@Srini’s+iPhone=LWVG427MVFAPZET2&, for tuser2, length is 35
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 1-108989: OTP Secret Attribute name: , length 15
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[498]: receive_ldap_user_search_event 1-108989: extracted attribute, name: userParameters, value: #@Srini’s+iPhone=LWVG427MVFAPZET2&,
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1196]: get_otp_attribute 1-108989: OTP Secret Attribute name: , length 15
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[1334]: build_ldap_group_string 1-108989: While building the ldap group string for user tuser2, group attribute was null
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[515]: receive_ldap_user_search_event 1-108989: For user tuser2, group stringLength 0
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[527]: receive_ldap_user_search_event 1-108989: no group extraction for tuser2
Wed Feb 21 07:42:15 2018
/home/build/rs_120_53_3_RTM/usr.src/netscaler/aaad/ldap_drv.c[533]: receive_ldap_user_search_event 1-108989: Authentication is disabled for user tuser2, finishing ldap authentication
Srini
February 21, 2018Hi George – I resolved the issue. LDAP Bind account didn’t had permissions to OU where that one user account was. Thanks.
Melvin
March 2, 2018Hi George,
I followed your article and got OTP setup configured in my environment. It’s working well for almost everyone, except for one specific user .
When he try to register for OTP at manageOTP website, instead of prompting for device addition his session gets re-directed to challange OTP Page . Could you please suggest
George Spiers
March 3, 2018Clear the browser cache and try again, making sure that the URL for the Gateway is appended with /manageotp
Melvin
March 7, 2018Hi George,
We were getting LDAP error 49 for the impacted users, different user account in same OU was not getting any error message . It seems that the issue was occuring because the account expiration date for the impacted user was in the past, changing that corrected the issue
George Spiers
March 7, 2018Interesting, so if an account has expired no error was received from NetScaler? The page just reloaded?
Disabled account flagging LDAP error 49 is normal and I documented it a while back – https://jgspiers.com/digging-in-to-citrix-logon-process/
Andrew W
May 3, 2018Thanks George for the great article. One question around restricting ManageOTP URL via group membership, where do you configure that specifically in the above configuration?
Andrew W
May 3, 2018Resolved this by just creating a 2nd Authentication Policy under the AAA server using a different LDAP policy (checks for group membershop)
Michael V.
May 9, 2019So could this be used to restrict users to a single OTP generator by having some automation that moved them from one group (that has access to ManageOTP) to another (that doesn’t) after they enroll an OTP device? Then it would require a call to a Help Desk to delete an OTP device and re-enroll?
George Spiers
May 9, 2019Your theory could work yes. If the userParameters (or another) attribute contains a value, remove user from ManageOTP group and if the string is empty, keep in group.
Michael V.
May 9, 2019It seems that without something like this, this implementation of using OTP for MFA has a glaring security hole. Time-based OTP is designed to be compatible with self-service enrollment, but that only works if that’s the *only* self-service function. With ManageOTP being available via single-factor authentication, even after an OTP device has been enrolled, it defeats the whole purpose.
Am I wrong? Is there a better solution than what I’ve proposed above?
George Spiers
May 13, 2019You can restrict ManageOTP to corporate only networks, or you could do something where users who are part of the “IsEnroled” AD group are challened with Username/Password + OTP for future self-service (using nFactor logic) and users who are not part of the group are challenged with 1FA. Some automation could add users to the IsEnroled group when the desired AD attribute for OTP is populated.
Srini
June 11, 2018Hi George,
I implemented NetScaler OTP and is live with few users. I noticed that we can bypass OTP by leaving it blank, it takes me straight in. I also tested by entering random numbers, still able to login.
George Spiers
June 11, 2018That normally happens if the LDAP factor (username/password) does not have a nextFactor configured which is another LDAP policy with authentication unchecked, but the OTP Secret field is complete with userParameters.
Srini
June 11, 2018To give you some background. My setup is not 2 factors upfront. Default schema is username only, based on user group extraction password only or password&OTP is presented to users.
Srini
June 12, 2018Thanks, after configuring next factor it was working as expected.
Pingback: NetScaler Native OTP – Prevent Enrollment of Additional Devices Externally | #1 Canadian Team of Trusted IT Advisors
MK
August 9, 2018Thanks for the nice write up. Having an issue running on 12.1.48.13. When trying to access to the /manageotp I am getting the http://1.1 service unavailable.
I do have my UG behind a CSvip. Any ideas of what I may be missing?
Anonymous
August 9, 2018Forgot to add in the || http.REQ.URL.contains(“manageotp”) in my CS Pol. Working now!
MK
August 9, 2018Forgot to add in the || http.REQ.URL.contains(“manageotp”) in my CS Pol. Working now!
Alun
August 16, 2018Hi George,
Thanks for the well written article. I have implemented OTP and am able to register devices and login using sAMAccountName as the username on the login page and am then successfully redirected to the StoreFront Store page.
For our purposes we would prefer to use UserPrincipalName for the username, our users are issued the UPN and it cannot easily be translated to the SAN. For example, my demo user’s UPN could be demoalun@example.com and the SAN would be DOMAIN\demoalun_demo1.
I modified the LDAP Actions to use UserPrincipalName in the ‘Server Logon Name Attribute’, for the ‘SSO Name Attribute’ I have used cn, sANAccountName and UserPrincipalName. In all cases the login succeeds but when the StoreFront Store page is displayed I get the ‘Cannot complete your request’ error popped up.
Looking in the debug trace on the StoreFront server it looks like the first part of the UPN (demoalun) and the domain name (DOMAIN) are being passed in which I believe StoreFront is interpreting as sAMAccountName and Domain attributes, which then fails to authenticate.
Have you been able to get Native OTP working with UPN for a StoreFront virtual server?
Thanks and regards
Alun
George Spiers
August 16, 2018Should work, have you set UserPrincipalName as the Logon Name Attribute on your LDAP and OTP Challenge profiles? So the LDAP policy which is bound directly to the AAA vServer and then the second LDAP OTP Challenge policy that is part of your Policy Label.
Alun
August 16, 2018Yes, I have set Logon Name Attribute to UserPrincipalName on all three LDAP Server profiles (LDAP Auth, LDAP Challenge and LDAP Manage).
I am able to login to manageotp using UPN and manage devices.
The login to the NetScaler virtual server is also working, if I use a wrong OTP code the login fails. It’s when the NetScaler hands off to StoreFront and the store is displayed the ‘Cannot complete your request’ error is displayed.
Regards
Alun
Alun
August 16, 2018I have it working now, I had to add sAMAccountName to the ‘SSO Name Attribute’. although I thought I had tried that yesterday, I must have misspelled it or something.
Anyhow, thanks for a great article and for jumping in to assist so quickly.
Now I just need to separate the token request from the user credentials so I can give end users the choice, and create/use a different attribute for the OTP Secret as userParameters is already used for something else.
Thanks
Alun
sunil
September 26, 2018Hi , Suppose any user has password of other user and if he register his device then he can easily login and check other user data. How N-Factor prevents it.
George Spiers
September 26, 2018nFactor does not prevent is specifically. For OTP, you can lockthe enrolment page down to corporate devices only, internal access only from corporate network, protected by time-based group membership, etc.
Alun
September 26, 2018Hi George,
Can the manageotp page be protected with OTP?
I have changed my implementation to request the username then, depending on whether OTP device(s) have been set in the OTP Secret AD attribute, present either a 2 field credentials or 3 field credentials + OTP token form.
This works when hitting the root URL, the appropriate form is displayed and when correct details are entered the user is forwarded to StoreFront.
However, for manageotp it only works when the OTP Secret AD attribute is empty and the 2 field credentials form is used. If the attribute is populated and the 3 field credentials + token form is used, the user authenticates but gets forwarded to StoreFront rather than the manageotp page.
Thanks
Alun
Melvin Sebastian
January 17, 2019Hi George,
Have you ever seen “userparameters” field getting populated with junk values,like the one given below .
P CtxCfgPresent㔵攱戰㠢 CtxCfgFlags1〰㠦〲〹 CtxShadow㄰〰〰〰. CtxMaxDisconnectionTime〰㡢挴愰* CtxMinEncryptionLevel㄰
Offlate we have multiple users who report enrollment issues with error “failed to add device” , fix for which is to remove the junk values from userparameters field .
Anonymous
January 17, 2019Hi Melvin,
The userParameters attribute can be used to store terminal services configuration data which would overwrite the stored OTP keys. In our environment we use one of the extensionAttributes to store the OTP keys.
Regards
Alun
George Spiers
January 25, 2019Hello – the userParameters attribute can be used by Terminal Services. It looks like you might have an old Citrix farm running and TS is injecting values into that parameter. Best to pick a different parameter for OTP, one that is untouched.
a.diallo
January 22, 2019Thank you for this blog.
Do you have any solution to get this work with iOS native Receiver? With the new Workspace App for Windows and Mac it works well. I guess it is the twist with the passcode and otp field. But I’m not sure how to solve this. Maybe with attribute fields?
George Spiers
January 28, 2019nFactor isn’t supported with iOS yet so unfortunately not.
Jani Kohonen
April 3, 2019Hi, thanks for your blog post! I followed your instructions and now I want to restrict /manageotp page via AD groups, so external users can enroll the deive only if they are members of the particular group. I think I could use expression “HTTP.REQ.USER.IS_MEMBER_OF(“AD_Group”)”, but in where I actually configure it? Also, I would like to get it to work like when they belong to the group they can enroll, but after succesfull enrollment, user will be removed from the group and they continue to use two-factor but cannot enroll any new devices. Any advice highly appreciated! 🙂
George Spiers
April 5, 2019Hello. Yes, you could use that expression. You could create a new Policy Label for OTP enrolment which does not evaluate any additional LDAP policy if user is not a member of the group. The AAA vServer would have Authentication Policy “LDAP_SAN_Auth_ManageOTP” followed by newly created nextFactor/Policy Label. This Policy Label has another LDAP policy which only evaluates if user is member of the group.
Jammy
May 24, 2019How to find a user who already issue the OTP?
George Spiers
May 27, 2019You can look at the userParameters (or a different one you selected) attribute to see who has already registered with OTP.
Pingback: Native One Time Passwords (OTP) – Citrix Gateway 13 – Carl Stalhood
Hartland West
June 4, 2019We deployed Native OTP in March, and it seems to have broken access via the Mobile Receiver. This has caused our execute staff to revolt, to set aside thier concerns for security so they can keep using the mobile receiver.
Julian Gomez
August 6, 2019Why is it necessary to use RfWebUI porthal theme? is it any specific reason to avoid using the other porta themes?
George Spiers
August 16, 2019The RfWebUI theme allows for more customisation and is recommended to be used with Native OTP.
Roman
September 18, 2019Hi Carl / George.
I have a problem with the otp on citrix receiver. When I login for first time, receiver shows me the user, pass and otp field, and everything works fine, but then, when I logoff the session and try to connect again, it only shows me the user and pass field, and the otp field doesn’t shows again.
George Spiers
September 29, 2019What version of Receiver/Workspace app are you using, and what build of ADC?
Ilyas Ahmed
October 5, 2019Hi Geroge,
Thanks for your great article!!
I have followed your instructions and built the environment to run the Netscaler Native OTP authentication. The authentications are working on windows base system via browser. however, I am not able to authenticate while using Android mobile and Iphone devices. getting contact your help desk error.
I wanted to know does it supports only windows based computers? or is there any configuration do I need to do on Netscaler to fix this issue.
Regards,
Ilyas Ahmed
George Spiers
October 6, 2019Hello – what version of Workspace app and ADC are you running?
Ilyas Ahmed
October 7, 2019Hi George,
Thanks for kind support.. Appreciate!!
It is resolved by updating the receiver. however, still I am using ADC version 12.1.51.19.
I want to know about users AD attribute device enrollment procedure. In my environment I have not set userParameters>=#@ in users properties on AD but still users can enroll their devices by using manageopt portal.
My requirement is to first I will add users paramenters in requested users properties then users can enroll their device. is that possible?
Regards,
Ilyas Ahmed
George Spiers
October 9, 2019Users can always enrol their device, but I found that using the Search Filter in this way prevented any user who had not yet enrolled from logging on to Gateway.
Anbuselvan
October 10, 2019Hi George,
Congrates for this article.
I’ve configured NS GW with Google Authentificator and it works as it should be.
How do I configure to disable or restrict if user has already registered his device ?
Thanks again
Anbu
George Spiers
October 15, 2019ADC 13 allows you to restrict the number of devices a user can register.
Security -> AAA – Application Traffic -> Change authentication AAA OTP Parameter
Anonymous
May 2, 2020Hi George,
It works for me the dual authentication with Google OTP on Netscaler ADC v13.0-47.24. I did some customization like filtering AD Group, disable Delete button for users on portal and etc.
I’m wondering, I case of incident in this solution, how to troubleshoot it? Does Citrix do the support? Is it Google OTP is right solution in production environments?
Thanks again George.
George Spiers
September 9, 2020Hi. This is Citrix OTP, so Citrix support it providing you have ADC maintenance agreement. Google Authenticator, like Microsoft Authentication and even Citrix SSO, supports RFC 6238 TOTP so can be used with Native OTP.
IF
January 29, 2020Hi George,
I’ve done all the steps you said, everything is working (thank you). Just one thing isn’t, when the userparameter box is empty within AD on a user, it can’t logon the manageotp side, when i manually fill in some random text, it’s working. Any idea what i may did wrong?
George Spiers
February 17, 2020For the ManageOTP side, are you authenticating with the LDAP action that has the Search Filter?
IF
February 17, 2020Yes we have. For some strange reason it’s working now, i deleted all the config and did the steps again.
Rickard
March 17, 2020Damn i feel bad, tried both yours and carl and neither works for me
Michael Shen
March 23, 2020Hi George, thanks for the good work. I have a question, is it possible to remove the function for user to delete device? so once its set , its there and they have to call service desk to have it reset for them. that way it will be a bit safer than anyone can single sign in to manageotp and delete device setup a new device, even I set 1 device per user. thanks
George Spiers
May 19, 2020You could probably lock down the manageotp page based on if the OTP Secret is null or not.
Sander
April 13, 2020Thanks for the post, i am almost there, i get the page “My Registerd Device” when i click the add sign, i can enter a name but when i click de + sign i get a error “Failed to add …” can you help me.
Anonymous
April 13, 2020most likely its the service account you use does not have write access to userparameters attribute
Anonymous
April 14, 2020One tip is to check if you have encrypted otp checked and make sure you have a key imported for that
Sander
April 14, 2020Thanks i didn’t imported a key to encrypte the OTP.
Stefan
April 21, 2020Where can I find this setting? I also get the ‘Failed to add…’ error.
Stefan
April 21, 2020Found it and now i’m able to register a device! Thanks for the tip 😉
Stefan
April 21, 2020Hi George, Is it possible to specify an IP range for which no OTP has to be entered? It is now enabled for all connections to my Access Gateway.
George Spiers
September 9, 2020You just need to create another authentication policy and give it a priority of 105 on your AAA vServer for example. That policy will be matching on the IP range.
Mahmoud
May 10, 2020Hi, thanks for your blog post!
Can we use OTP for a virtual server (load balancing for web server)?
Alessandro Tomba
May 21, 2020HI,
thanks for your article.
Is it possible to send an email to the users when a device is added to /manageotp portal?
Pascal Schmidt
May 25, 2020Hi George!
We configured multiple authentication policies to redirect to different domains. The issue is that we can only address one domain at the same time and only the one with the highest priority. For the other domains we get a reject with error code 4009. Is there a way to address different domains with the same AAA-server or do we need a separate AAA for each domain?
Thanks a lot!!
Anonymous
May 28, 2020Solved it! GO TO EXPRESSION in policy binding settings was set to “END”! Read first, then ask 😉
Florian Meyer
June 4, 2020Hi George,
do you have an idea about using manageotp in a single url (internal/external netscaler) setup?
If I call the gateway url from internal with /manageotp there is no such site, because from the internal network I get the internal netscaler – but the native otp is set up on the external netscaler.
Does anyone has an idea?
To use another url is even not possible, because when I call the other url (resolving to external netscaler) I can manage my otp, but when I log out, I stay on the other url, but I would need to be redirected to the original gateway url.
Anonymous
June 17, 2020Hi George,
when i add new device and click GO to get QR code I receive no response.
I’ve checked the theme for AAA vserver and the access gateway have “RfWebUI“
What else could the issue be.
Kedar
June 17, 2020Hi George,
when i add new device and click GO to get QR code I receive no response.
I’ve checked the theme for AAA vserver and the access gateway have “RfWebUI“
What could the issue be?
Kedar
June 17, 2020managed to solve it 🙂 it was the service account permissions
Kedar
June 17, 2020Also would this native OTP config, work with double Hop DMZ configuration ?
Or would some changes in the above specified configuration be required?
Pingback: EUC Weekly Digest – August 5, 2017 – Carl Stalhood
Juan
December 9, 2020Hi George,
Thank you for this great article.
We try to integrate MFA with our working SSO configuration but seems SSO is not working when we have MFA.
Single Sign ON(SSO) is working smoothly without MFA.
We are able to to authenticate using MFA with SSO authenticator app(Citrix SSO authenticator/Microsoft authenticator )but when when we launch the applications via gateway SSO doenst work, what would be the issue on this? We follow everything based on this article.
Hope you can help me on this.. Thanks Goerge,, 🙂
Regards
Fred
February 25, 2021Hi Georges, very useful article even few years after u wrote it ! Thank you
Ojido
June 25, 2021Hi George, thanks very much for your time and for the wonderful article. is it possible to secure the / manageotp registration page with the user certificate as nFactor before the loginschema “username and password”. For external User on private computer. I am looking at this way in such a way that the user certificate would be sent to the user via email and the user can install his /her certificate on his/ her private computer. The user certificate would serve as the first factor and the username and password as the second. Thanks.
Martijn
January 4, 2022What’s the status with Citrix Workspace App? It doesn’t seem to work with that.
rami
May 10, 2022Hello George,
Thanks for the introduction, everything seems to have worked.
Now I try it the other way around, so first factor OTP then LDAP , so that the LDAP factor can not be blocked by repeated failed attempts.
so I did the following:
1.authpol: LDAP no auth
2.polllabel: OTP verify
3, polllabel: LDAP auth
but unfortunately it did not work, I get the error message “Failure_reason “External authentication server denied access” on level polllabel: LDAP auth
Any idea what the reason is ? Looking forward for your comments. Thanks.
Pedro
October 5, 2022Hello George,
Thanks for the article.
in a Netscaler native OTP scenario, in the registration part (after the user has entered their Active Directory credentials), is it possible for the user to register or receive the QR code in their email? or some other method by initial mail to register?
Thanks