I’ve been meaning to write up about this for a while now ever since creating the original Citrix FAS and SAML related blog posts upon the release of StoreFront 3.9.
One of the Microsoft Active Directory features that can be used to extend the functionality of Citrix Federated Authentication Service is a feature called Authentication Mechanism Assurance.
Using this feature, we can control access to the likes of files, folders and other security controlled objects based on if our logging on users have authenticated with a certificate or not. Since FAS issues certificates to our users and presents those to the VDA, there is very little extra work needed to make use of this.
Think of the scenario which we will follow in this post. We have file shares that should only be accessed by users who have authenticated with a Smart Card. If a user does not have a Smart Card, they use username and password as normal, but they shouldn’t be granted access to the confidential file shares.
Before you begin, you need to deploy Citrix FAS and ADFS. To do that, see https://jgspiers.com/adfs-authentication-direct-to-storefront-3-9-using-saml-and-citrix-federated-authentication-service/
Note: This solution uses ADFS. As users browse to StoreFront they are redirected to ADFS for authentication. Once they provide credentials SAML is used to send an assertion to StoreFront which will in turn generate a certificate to our authenticating user which is used to authenticate with the VDA when an application and/or desktop is launched.
Note: In this example I am demonstrating access to a file share. You could use this feature to control access to files, file shares, applications, printers and so on.
Once you have FAS fully working in your environment, you can carry on with the below.
Requirements:
- FAS fully functional including ADFS and Microsoft Active Directory Certificate Services.
- Windows Server 2008 R2 Domain Controllers at a minimum.
- Domain Functional Level set to Windows Server 2008 R2 at a minimum.
Open the Active Directory Certificate Services console and right-click Certificate Templates -> Manage.
Locate template Citrix_SmartcardLogon and right-click Properties. Click the Extensions tab, highlight Issuance Policies and click Edit. 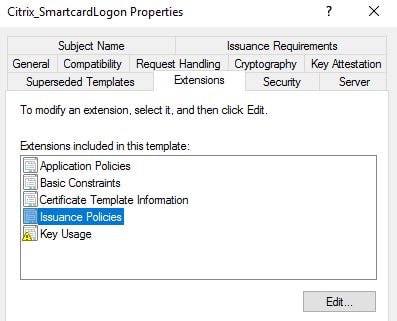
Click Add to add a new Issuance Policy. 
A couple are created by default, and you can create your own. For now we can simply use the Medium Assurance policy. Highlight this policy and click OK. 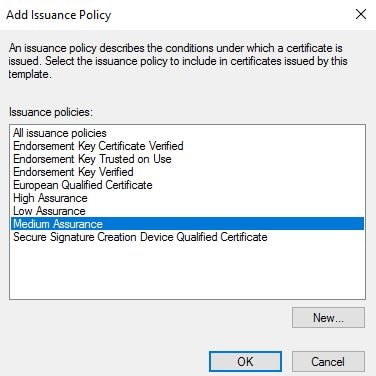
Click OK. 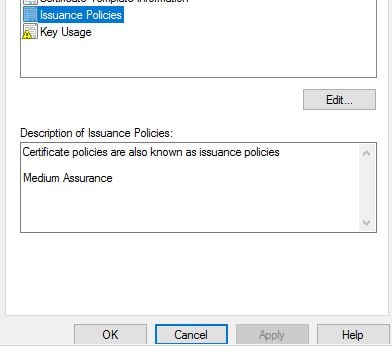
The next step involves the creation of two scripts. The scripts are called Get-IssuancePolicyToGroupLink.ps1 and Set-IssuancePolicyToGroupLink.ps1. Both scripts are available from TechNet Step 3. Create both scripts on your Domain Controller under C:\.
Now on your Domain Controller launch Active Directory Module for Windows Powershell. 
Type command Get-IssuancePolicyToGroupLink.ps1. ![]()
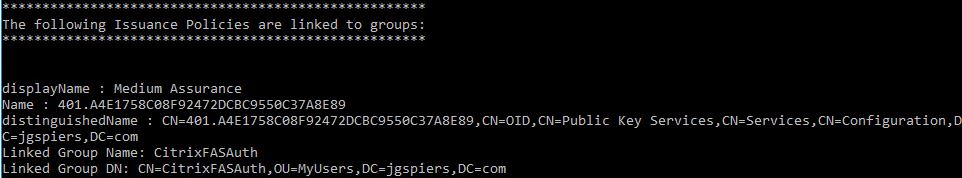
This script will list the Issuance Policies available in your domain and display any that are linked to groups. Just to confirm, there are no Issuance Policies linked to groups at this stage. 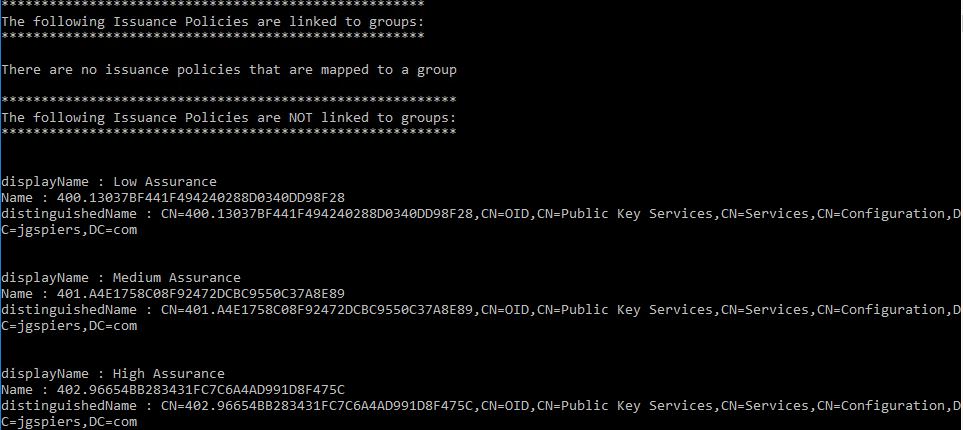
To link an Issuance Policy (in our case the Medium Assurance policy) to groups we need to first create a group in Active Directory. The group must be a Universal Security group. This group will then become a part of a user’s kerberos ticket when they log on to the VDA with a certificate. The group will also be granted access to the confidential file share.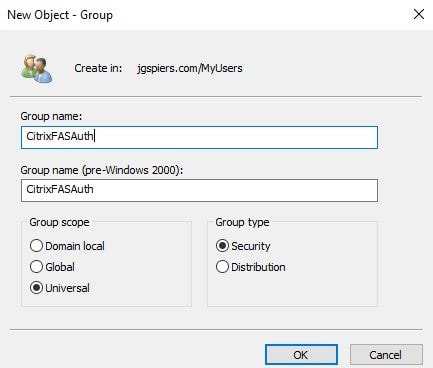
Once the group is created return back to PowerShell and this time we will be running the Set-IssuancePolicyToGroupLink.ps1 script. For parameter IssuancePolicyName specify Medium Assurance. For parameter groupOU specify the Organizational Unit name that is home to the security group you just created. For parameter groupName specify the Universal Security group name you just created.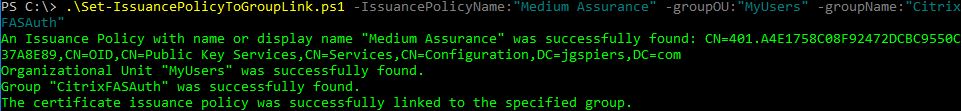
Next create a file share which is locked to only members of the Universal Security group as below. 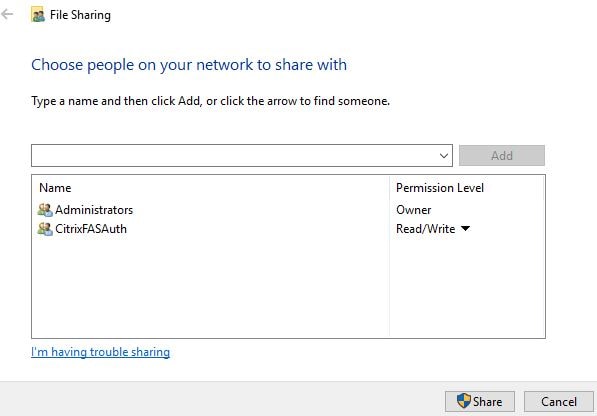
Click Done. Only members of CitrixFASAuth will be able to access the \\dc\confidential share. Only users who authenticate via Citrix FAS are added to the CitrixFASAuth group using Authentication Mechanism Assurance.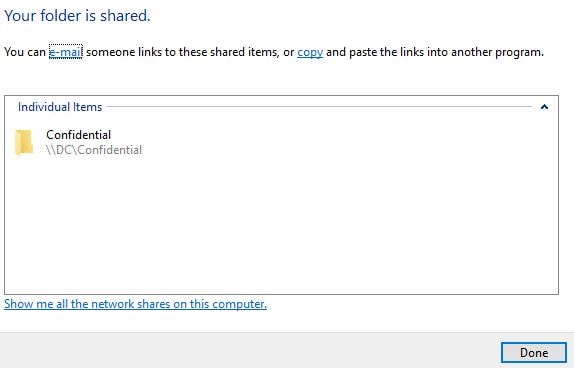
I proceeded to log on to the VDA using FAS. I also was able to access the Confidential file share. If accessing the VDA without authenticating using FAS, I was denied access.
Using whoami /groups when logged on to the VDA I can confirm that my account is added to the CitrixFASAuth group. As soon as a log off, I will not be a member of that group until I authenticate using a certificate again.![]()
Note: If you have issued certificates to users via FAS before configuring Authentication Mechanism Assurance, you will have to remove those cached certificates from FAS to allow new ones to be generates with the Issuance Policy extension included in the new certificate. You can use cmdlet Remove-FASUserCertificate on all FAS servers.
Qwerty
January 18, 2018It is worth noting that with a bit of effort you can tie dynamic group membership into the SAML assertions at Netscaler. We use this with GeoFencing.
tldr
February 1, 2018Great article. I find the FAS commandlets New/Get/Set/Remove-FasPolicyOid to be a little easier to use than the Microsoft scripts.
AW
July 23, 2018Does AMA work with FAS and smartcard login without configuring SAML?
George Spiers
July 23, 2018Yeah if a user is logging on with a certificate then AMA will work.