If you want to enable LDAP Secure for NetScaler authentication follow the below guide. Using LDAPS allows you to use the Allow password change option on NetScaler so Active Directory users can change their expired passwords. For this reason, and the security advantage, many people opt in to using LDAPS with NetScaler.
NetScaler Authentication Logging – https://jgspiers.com/netscaler-authentication-failures-aaad-debug/
NetScaler Logon Process and Failure Reasons – https://jgspiers.com/digging-in-to-citrix-logon-process/
NetScaler Gateway direct authentication to StoreFront instead of using LDAP policies – https://jgspiers.com/netscaler-gateway-authentication-direct-storefront/
It is wise to note that if you run in to any problems whilst configuring LDAPS/LDAP authentication or if you ever have authentication issues you should enable authentication logging on your NetScaler via the CLI to see what is going on.
To do this open the NetScaler CLI -> authenticate using sufficient credentials -> type shell -> type cd /tmp -> type cat aaad.debug and press enter.
Now every authentication attempt will be logged. As you can see below authentication is failing on my NetScaler with results such as receive_ldap_bind_event Got LDAP error. The reason being that I deliberately changed the LDAP bind account password so I could show you an example!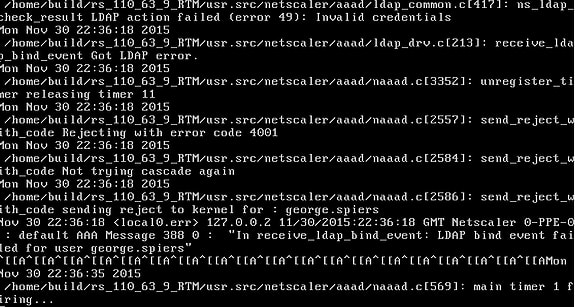
Now, back to LDAPS setup.
Firstly you need to install a certificate on your Domain Controller(s) to secure authentication traffic over SSL between the NetScaler and Domain Controller server(s).
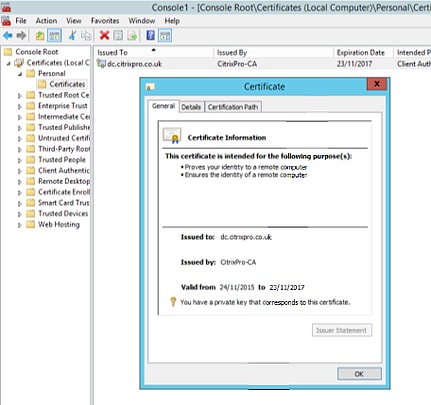
Depending on how your internal Certification Authority is set up there are multiple ways to request a certificate such as through IIS, Certificate Services Web Enrolment and Active Directory Enrolment Policies. Ensure that the certificate you do use provides Server Authentication and Client Authentication as the one shown below. Also ensure the Subject Name matches your domain controllers name.
Once you have your certificate in place navigate to NetScaler Gateway -> Policies -> Authentication -> LDAP and edit your existing LDAP server profile or create a new one.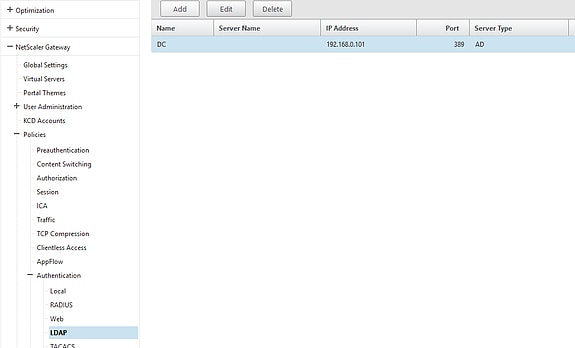
Under Security Type select SSL and the port will automatically change to 636.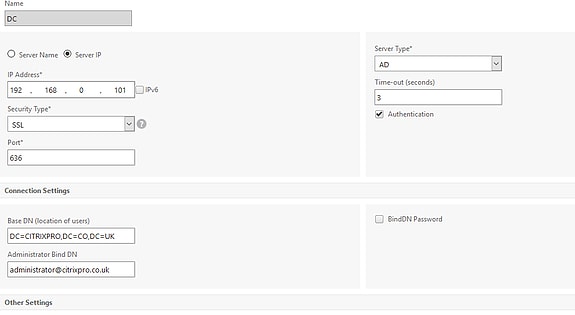
After selecting SSL you will see the option for Allow Password Change. Choose this if you wish to allow users to change expired Active Directory passwords.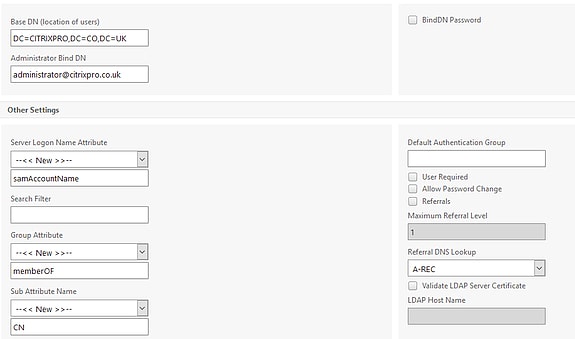
Now at the bottom of the configuration screen click Done and then save the configuration.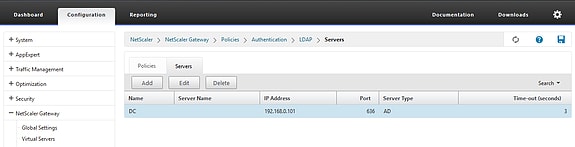
All being well you should now be able to authenticate over LDAPS. If you do get failures, refer to NetScaler authentication logging. Check also that any firewall between your NetScaler and Domain Controllers are not blocking TCP 636. Another thing you can do is use the ldp.exe tool to bind to a Domain Controller over SSL.
Pablo
October 16, 2017Did you import the CA root certificate (from the CA server) on the netscaler appliance? If so, where did you import it?
George Spiers
October 17, 2017That is right, you just import it under Traffic Management -> SSL -> Certificates -> CA Certificates.
Pablo
October 17, 2017And bind the ca certificate to the load balancing ldaps vs? I don’t need a server certificate just the CA certificate?
George Spiers
October 17, 2017If you are Load Balancing LDAPS then you need to create a server certificate which matches the FQDN of the vServer VIP, and bind that certificate to the Load Balancing vServer.
If you are not Load Balancing LDAP and simply creating an LDAPS enabled LDAP Server (Action/Profile) for authentication, you don’t need a server certificate for that, just a CA certificate.
Pablo
October 17, 2017Ok. Is done on my CA certificate? Do you have a reference page for this?
Pablo
October 17, 2017All my domain controllers have the certificate on them…. to add the VIP name on the san subject alternate name?
Pablo
October 17, 2017I have a wildcard cert that’s on my netscaler… but that’s not configured for ldaps. Ldaps domain controllers are using a certificate from our certificate authority server. The wildcard is for .eventreviewing.com and my domain controllers have internal certificate for each server separate:
Ldaps
Dc1.eventrewiewing.local
Dc2.eventrewiewing.local
Dc3.eventrewiewing.local
Pablo
October 18, 2017Sorry just having issue understanding netscaler ssl-tcp…. if I’m using a wildcard for my vserver ldaps with SSL_TCP and on the backend sever have ldaps with all 3 host have separate certificates on the domain controller. I shouldn’t have an issue correct? So if the 3 domain controller certificate expires soon I shouldn’t have to do anything on the netscaler correct? My vservers all use a 3rd party wildcard .eventreviewing.com and my domain controllers use a certificate from our ca dc1.eventreviewing.com
George Spiers
October 18, 2017Hi Pablo. Yes, should not be a problem to have a wildcard certificate on the LDAPS LB vServer so long as the clients connecting to that vServer trust the certificate. The individual domain controller certificates should not expire as if handled by ADCS, they will renew automatically themselves.
Sandeep
March 1, 2018Thank George !!
Jimmy
October 21, 2019My team is bumping into a problem when adding a trusted domain. We’re seeing this:
Server ‘xxx.xxx.xxx.xxx’ is reachable.
port ‘389/tcp’ is open.
Either ‘xxx.xxx.xxx.xxx’ is not an LDAP server or port ‘389’ is not an LDAP port.
Have you run into this before? We tried port 636 too and we also tried changing the security type from TLS to SSL and Plain Text with no change.
George Spiers
November 10, 2019Any firewall or routing issues between the two devices? Normally I would take a NetScaler trace and confirm via WireShark.
Nav
December 18, 2023Hello Jimmy, were you able to resolve this error : Server ‘xxx.xxx.xxx.xxx’ is reachable.
port ‘389/tcp’ is open.
Either ‘xxx.xxx.xxx.xxx’ is not an LDAP server or port ‘389’ is not an LDAP port.
abu abba
July 10, 2020hello george, i was able to configure sspr on citrix gateway in my environment but when i try to login or reset the password it says cannot complete request. i’d appreciate your help thanks much